 Remember the unsettling news of the Marina Bay Sands data leak back in November 2023? Over 665,000 rewards program members had their personal details exposed, including names, email addresses, phone numbers, and membership information.
Remember the unsettling news of the Marina Bay Sands data leak back in November 2023? Over 665,000 rewards program members had their personal details exposed, including names, email addresses, phone numbers, and membership information.
Just a few months ago, in March 2024, a similar incident struck closer to home, with Poh Heng Jewellery experiencing a data breach that compromised customer names, contact details, birthdays, and usernames.
These are just a few recent examples of how cybercrime is rising in Singapore. As our Smart Nation initiative expands and we rely more on technology, the need for robust cybersecurity has never been greater.
But have you ever wondered if, hacking can be a force for good? Believe it or not, there’s a whole world of ethical hacking out there, and it’s becoming an increasingly important field in Singapore’s IT industry.
In this article, we’ll delve into the fascinating world of ethical hacking, separating myth from reality.
We’ll explore what ethical hacking is, how it works, and why it’s crucial for Singapore’s cybersecurity landscape.
Whether you’re a complete IT beginner or simply curious about the world of hacking, this article is your gateway to understanding the ethical side of this ever-evolving field.
What is Ethical Hacking?
So, what exactly is ethical hacking? Ethical hacking, also known as white hat hacking, is the authorised practice of simulating cyberattacks on a computer system, network, or application.
Unlike malicious hackers (black hats) who exploit vulnerabilities for personal gain, ethical hackers are the good guys in cybersecurity.
Companies and organisations hire them to identify and fix security weaknesses before anyone can exploit them.
Think of it like testing your home security system. You wouldn’t wait for a break-in to happen before figuring out if your windows are easy to pry open or your locks are flimsy, right?
Ethical hackers perform a similar function in the digital world. They use their hacking skills to try and break into a system, legally of course, and report any vulnerabilities they find.
This allows the organisation to patch those holes and strengthen its defences before any malicious actors can take advantage.
BONUS
Ready to test your detective skills? Let’s try out this simple quiz!
Which of these is NOT a good password practice?
A) Using a mix of uppercase and lowercase letters.
B) Sharing your password with friends.
C) Using the same password for all your accounts.
What is Unethical Hacking?
Now, let’s meet the bad guys – the unethical hackers, also known as black hats. These are the ones we hear about in the news, launching cyberattacks that steal personal information, disrupt critical infrastructure, and cause millions of dollars in damage.
Unlike ethical hackers who work within the law and with permission, black hats have malicious intentions and exploit vulnerabilities for personal gain.
Common Unethical Hacking Activities
Imagine a group of tech-savvy criminals breaking into a bank’s online system, not to fix it, but to steal money! That’s essentially what unethical hackers do.
Here are some common unethical hacking activities:
Data Breaches
Stealing sensitive information like credit card details, passwords, or even medical records is a major black hat tactic. This can lead to identity theft, financial loss, and a whole lot of stress for victims.
For example, the E-commerce platform Carousell suffered a data breach where hackers gained access to customer information. This resulted in the personal data of over 2.6 million users (Singapore, Malaysia, Taiwan and Philippines) being exposed and potentially sold online. This incident highlights the importance of companies prioritising cybersecurity measures to protect user data.
DDoS Attacks
Remember the time a major local online retailer’s website went down for hours? That could have been a DDoS (Distributed Denial-of-Service) attack, where hackers try to overwhelm a system with traffic, making it inaccessible to legitimate users.
For example, in November 2023, there was a seven-hour disruption in Singapore’s public healthcare websites where attackers launched a DDoS attack, overwhelming servers with junk traffic and hindering access for legitimate users.
Ransomware
This nasty form of attack involves encrypting a victim’s data, essentially holding it hostage until a ransom is paid. Imagine a hospital being unable to access patient records because of ransomware – a chilling scenario!
Despite a slight decrease in reported cases (132 in 2022 compared to 137 in 2021), ransomware remains a major threat in Singapore, mirroring a global trend with a 13% increase worldwide. Small and medium-sized businesses (SMEs) in manufacturing and retail are particularly vulnerable.
These businesses often possess valuable data and intellectual property (IP) that cybercriminals can exploit for extortion. Unfortunately, many SMEs lack the resources to counter sophisticated cyberattacks.
The consequences of unethical hacking are far-reaching. Individuals can suffer financial loss, identity theft, and even emotional distress. Businesses can face hefty fines, reputational damage, and even operational shutdowns.
On a larger scale, cyberattacks can disrupt national security and critical infrastructure, causing widespread chaos.
Dealing with Black Hatters
Unethical hacking isn’t just about flashy attacks on national infrastructure. It’s a constant threat lurking in the everyday digital landscape, especially for businesses.
These are the criminals we hear about stealing sensitive corporate data, disrupting critical business operations, and causing financial losses for companies.
Imagine a scenario where a hacker gains access to your company’s network, potentially compromising confidential client information, intellectual property, or even employee data.
This could lead to hefty fines for data breaches, reputational damage for your company, and even job losses.
As an ethical hacker or cybersecurity specialist, you’re the frontline defence against these threats. Here’s what you can do to protect your company:
Proactive Defence
Penetration Testing & Vulnerability Assessments
Regularly conduct penetration testing and vulnerability assessments to identify and address weaknesses in your company’s systems before black hats exploit them. Think of it like a pre-emptive strike against potential cyber threats.
Security Awareness Training
Educate employees about common social engineering tactics and best practices for cybersecurity hygiene. Empower them to become active participants in your company’s defence against cyberattacks.
Patch Management
Ensure all software and systems are kept up to date with the latest security patches to plug any potential holes malicious actors might try to exploit.
Reactive Response
Incident Response Plan
Develop a clear and well-defined incident response plan that outlines how to identify, contain, and recover from a cyberattack. This plan should include roles, responsibilities, and communication protocols for all stakeholders involved.
Digital Forensics
In the unfortunate event of a cyberattack, you’ll need to investigate and analyse digital evidence to understand the scope of the breach, identify the attackers, and prevent similar incidents in the future.
Communication & Transparency
Effective communication is crucial during and after a cyberattack. Keep your company’s leadership, employees, and potentially affected customers informed about the situation clearly and transparently.
By implementing these proactive and reactive measures, you can significantly strengthen your company’s cybersecurity posture and make it much harder for unethical hackers to infiltrate your systems and compromise sensitive data.
What is the Difference Between Ethical Hacking and Unethical Hacking?
Now that we’ve met both sides of the hacking coin, let’s see how they stack up:
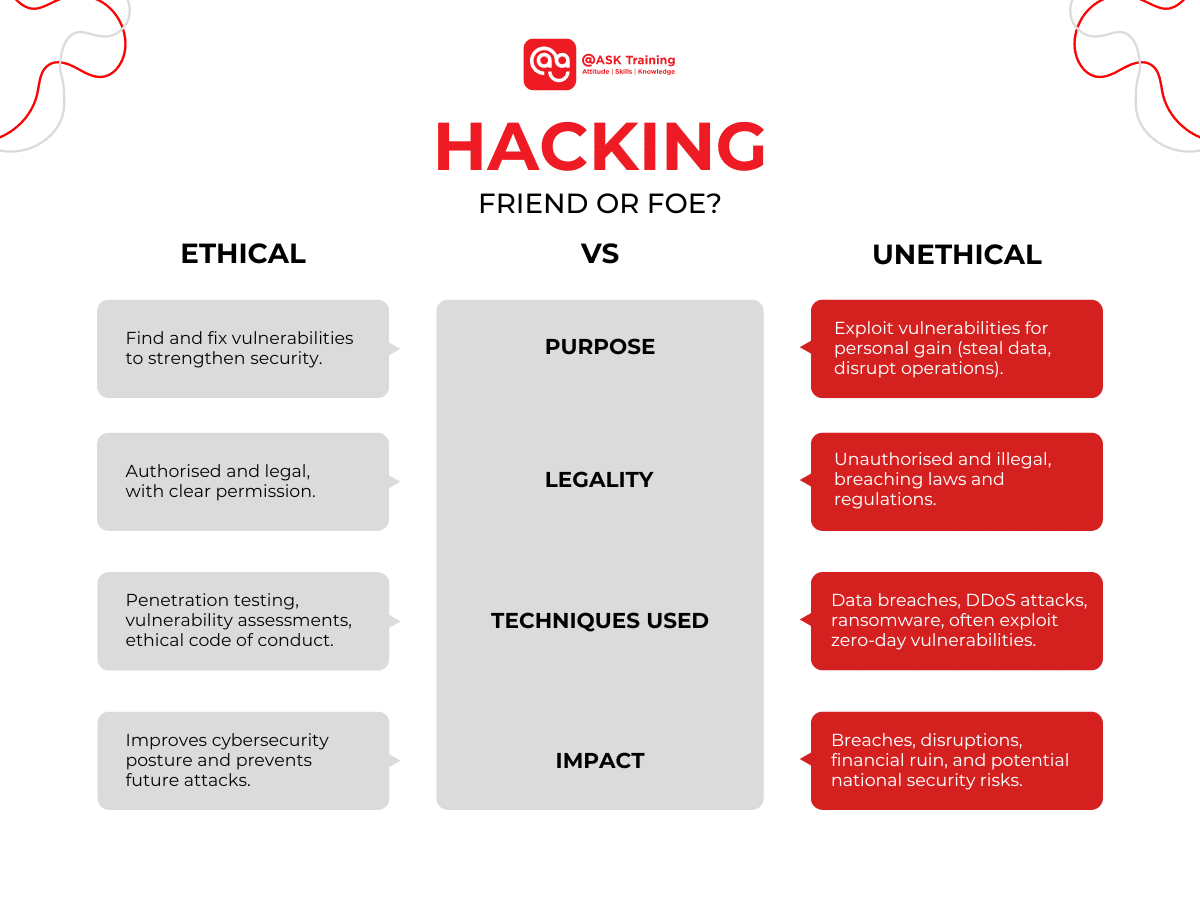
Purpose
Ethical Hackers: Identify and fix vulnerabilities before attackers exploit them, strengthening an organisation’s cybersecurity.
Unethical Hackers: Exploit vulnerabilities for personal gain, steal data, disrupt operations, or hold data hostage.
Legality
Ethical Hackers: Operate within the law, obtaining permission and following ethical codes for responsible and transparent actions.
Unethical Hackers: Gain unauthorised access, violating laws and regulations. Unethical hacking is a crime.
Techniques Used:
Ethical Hackers: Use tools like penetration testing (simulating cyberattacks) and vulnerability assessments (scanning for weaknesses) to identify and fix problems.
Unethical Hackers: Employ destructive methods like data breaches, DDoS attacks, ransomware, and social engineering to steal data or disrupt operations. They often exploit zero-day vulnerabilities.
Impact:
Ethical Hackers: By identifying and fixing vulnerabilities, they help organisations prevent cyberattacks and protect sensitive data. This strengthens the overall security posture of the digital world, making it a safer space for everyone.
Unethical Hackers: Has devastating consequences. Data breaches expose personal information, disrupted operations cost businesses money, and attacks on critical infrastructure can threaten national security.
Why Ethical Hacking is Important (and Cool!)
As we’ve seen, ethical hacking plays a crucial role in safeguarding our digital world. It’s not just about fancy tools and complex techniques; it’s about strategic thinking, problem-solving, and a passion for cybersecurity.
But why exactly is ethical hacking so important, especially in a country like Singapore actively building its Smart Nation defences?
Here’s why ethical hacking is not just cool, it’s critical:
The Rise of Cybercrime
With our increasing reliance on technology and the constant evolution of cyber threats, the demand for skilled ethical hackers is skyrocketing.
Take this recent report by the Singapore Police Force for example:
-
- Total Scam and Cybercrime Cases: In the first half of 2023, the number of scam and cybercrime cases increased by a staggering 69.4% to 24,525 cases, compared to 14,481 cases in the same period in 2022.
- Amount Lost: While there’s a silver lining, the total amount reported to have been cheated decreased by 2.2% to SGD 334.5 million, from SGD 342.1 million in the same period last year.
- This indicates that awareness campaigns might be having a positive impact on reducing financial losses.
- Top Scam Types: Job scams are the most common, accounting for 5,737 cases, followed closely by e-commerce scams (4,516 cases) and fake friend call scams (3,855 cases).
These statistics highlight the diverse tactics cybercriminals use to target Singaporeans.
Therefore, ethical hackers are the frontline defence against cyberattacks, proactively identifying and patching vulnerabilities before black hats can exploit them.
Singapore’s Smart Nation Ambitions
As Singapore strives to become a leading Smart Nation, robust cybersecurity is crucial. Ethical hackers play a vital role in securing our critical infrastructure, from transportation networks and power grids to financial systems and e-government services.
The Challenge of Staying Ahead
Cybercriminals are constantly developing new methods and exploiting zero-day vulnerabilities. Ethical hackers act as the “friendly fire,” using their skills to mimic real-world attacks and identify weaknesses before they can be used for malicious purposes. This constant testing ensures our defences stay ahead of the curve.
From what we have explored so far, did this article pique your interest in becoming an ethical hacker or passionate about cybersecurity? Let’s explore more in the next section.
Career Paths in Ethical Hacking
Singapore’s growing IT sector offers a diverse range of career paths for those passionate about cybersecurity and ethical hacking.
Job portals like JobStreet list numerous ethical hacking job opportunities in Singapore, with salaries ranging from SGD 5,000 to SGD 10,000 per month, depending on the specific role and employer.
Here are just a few career paths:
-
- Penetration Tester: Simulate real-world cyberattacks, attempting to breach an organisation’s defences and identify exploitable vulnerabilities.
- Security Analyst: Analyse data from various security tools, identify potential threats and recommend security measures to mitigate risks.
- Security Architect: Design and implement comprehensive security solutions to safeguard critical infrastructure and data.
These are just a few examples, and the specific career path you choose will depend on your interests and skill set.
But one thing is certain: the world of ethical hacking offers a rewarding and exciting career for those who are passionate about building a safer digital future!
Learn more about starting a career in cybersecurity in our article on Cybersecurity Essentials for Beginners.
Recent Ethical Hacking Developments (June 2025)
The field of ethical hacking in Singapore is advancing rapidly in 2025, driven by AI innovation and strong government support to strengthen the nation’s cyber defences.
Here are the key developments shaping the industry:
AI-Driven Tools Revolutionising Ethical Hacking
- Harmony Intelligence, a Singapore-based startup, secured US$3 million in funding (March 2025) to develop AI-powered penetration testing tools that automate vulnerability detection and threat analysis in real time.
- Platforms like PenTest++ now combine generative AI with human expertise, enabling faster and more scalable security assessments for enterprises.
Government & Talent Development Initiatives
- The Cyber Security Agency of Singapore (CSA) continues to expand its Cybersecurity Development Programme, certifying public-sector IT professionals in ethical hacking and deploying them across national cybersecurity teams.
- As part of Privacy Awareness Week 2025, @ASK Training collaborated with the National Library Board (NLB) and the Infocomm Media Development Authority (IMDA) to host the webinar “Intro to Ethical Hacking: Think Like a Hacker“, educating the public on cyber threats and ethical hacking principles.
These advancements highlight Singapore’s commitment to fostering a robust cybersecurity ecosystem, where ethical hacking plays a crucial role in safeguarding digital infrastructure.
Choose Your Side!
Ethical hacking is the shield that protects our digital world, while unethical hacking is the sword that seeks to tear it down.
The choice is clear: Singapore needs more ethical hackers, individuals who are passionate about cybersecurity and want to make a positive impact.
If you’re curious about learning more and potentially starting a rewarding career in ethical hacking, check out @ASK Training’s courses and enjoy up to 95% SkillsFuture Funding!
We also offer the SkillsFuture Career Transition Programme to support your career switch with our range of IT certifications:
- Certificate in Infocomm Technology (Infrastructure and Operations)
- Advanced Certificate in Infocomm Technology (Infrastructure and Operations)
- Diploma in Infocomm Technology (Infrastructure and Operations)
Remember, the future of cybersecurity lies in your hands. Will you be a white hat or a black hat? The decision is yours!