When most SME owners in Singapore hear “AI in cybersecurity,” their eyes glaze over. It sounds too abstract, too expensive, or too futuristic.
But the truth is, AI is no longer optional. It is increasingly essential. Scam losses in Singapore now run into the hundreds of millions of dollars per year, and cyberattacks have become so common that over 80% of organisations reported incidents in the past year. Without smarter defences, even a small business can be crippled overnight.
This article aims to bridge the gap by showing what AI-powered cybersecurity really looks like for SMEs, the threats to watch out for, legal guardrails, and a realistic roadmap to get defensible fast.
Let’s begin by demystifying what AI in cybersecurity actually does for a business like yours.
What is AI in Cybersecurity and Why It Matters for Singapore SMEs
At its core, AI in cybersecurity is advanced pattern recognition. It identifies subtle anomalies humans can easily miss—like a login from a new country, an unusual PayNow transfer, or a subtly malicious email. For your business, this means catching attacks early, before they escalate into major accidents.
This capability is critical in today’s landscape. Singapore’s position as a tech hub also makes it a high-value target, with scam losses tallied at S$651.8 million in 2023 alone (Singapore Police Force).
With at least 8 in 10 Singapore organisations facing a cybersecurity incident annually, the question is not if, but when your SME will be targeted.
This is where AI threat detection becomes a practical shield for your daily operations:
- It applies natural language processing to spot sophisticated, AI-generated phishing emails targeting your team.
- It establishes a “normal” baseline for your user behaviour and flags deviations, triggering extra checks for suspicious logins.
- Through automation, it can instantly block a fraudulent transaction on your e-store or quarantine a compromised device, all without waiting for human approval.
However, AI is not magic. Its strengths in speed and scale are balanced by its need for human oversight. False alarms can happen, and novel attacks might slip through. This is why the most effective strategy uses AI security tools for fast triage and containment, while your team remains in charge of final judgment, customer communication, and context.
For Singapore SMEs, leveraging AI in cybersecurity is no longer a futuristic concept but an essential step for building a defensible and resilient business.
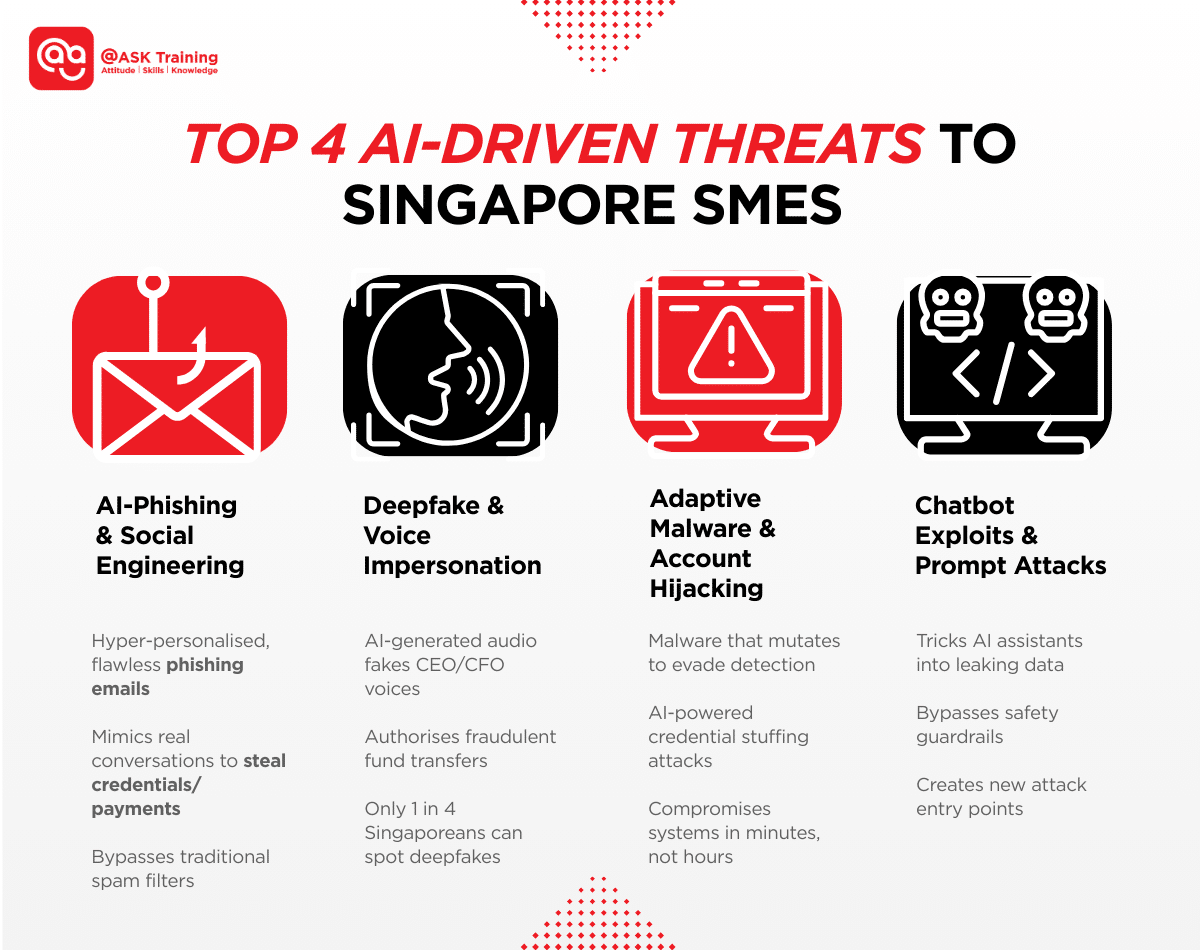
The Top AI-Driven Threats Hurting Online Businesses
Cybercriminals are now actively using AI for cyber-attacks, making their methods more sophisticated, targeted, and difficult to detect.
These are the key threats every Singapore SME should understand:
#1 AI-Generated Phishing and Social Engineering
Attackers now use large language models to craft phishing emails that are grammatically flawless, context-aware, and highly personalised.
These emails can simulate legitimate conversations to build trust before manipulating recipients into revealing credentials or authorising fraudulent payments.
The realism of these messages is their greatest weapon, making traditional volume-based filtering less effective.
#2 Deepfake and Voice Impersonation
This represents one of the most alarming developments. Attackers can use AI to create convincing audio deepfakes, impersonating a known voice like your CEO or CFO to authorise urgent fund transfers.
The risk is amplified by a demonstrated low public ability to identify synthetic media; in Singapore, only one in four people could correctly distinguish real from fake content in tests.
The government and CSA have issued joint advisories specifically warning about these scams.
#3 Adaptive Malware and Account Hijacking
Once inside a system, AI-powered malware can now mutate its behaviour in real-time to evade traditional detection tools.
Furthermore, attackers use AI to automate and accelerate credential stuffing and account takeover attacks, allowing them to compromise and move laterally across your services within minutes, not hours.
#4 Chatbot Exploits and Prompt Attacks
If your business uses AI-powered assistants, they can become a new vulnerability. Attackers can craft malicious prompts designed to trick these chatbots into bypassing their safeguards.
This can lead to the unauthorised release of sensitive information or the performance of restricted actions, creating a novel entry point into your systems if proper guardrails are not in place.
The good news is that you can start defending against these advanced threats almost immediately by focusing on a few key areas.
Quick Wins This Quarter (deploy first where losses happen)
You don’t need a massive budget or a long project to start leveraging AI for defence. Focus your efforts where your business is most vulnerable to immediate financial loss.
- Activate advanced phishing protection in your existing email platform (like Microsoft 365 or Google Workspace). Prioritise protecting high-value targets like finance@ and HR@ mailboxes first.
- Enforce Multi-Factor Authentication (MFA) across all systems. Enhance this with risk-based prompts that challenge logins from new devices, unfamiliar locations, or unusual times.
- Enable AI-powered anomaly detection on company devices and your network. Look for solutions that offer auto-isolation to instantly contain a compromised endpoint and prevent an attack from spreading.
- Implement payment fraud screening for your online store or marketplace. Make it a daily habit to review the “blocked orders” queue to fine-tune the system and ensure legitimate sales are not being interrupted.
These steps create a foundational layer of AI threat detection that works tirelessly to protect your most critical assets and revenue streams.
Once these quick wins are in place, the next step is to define how your team and these new tools will work together effectively.
Humans + AI: Getting The Balance Right
The most effective security strategy is not about replacing your team, but empowering it. The goal is to create a powerful partnership where AI security tools and human expertise each play to their strengths.
Let AI Handle The Speed, Humans Handle The Context:
- Use AI for the rapid triage of thousands of events and for initial containment actions.
- Reserve your staff for making final judgments, approving critical actions, and managing sensitive customer communications.
Establish A Clear, Simple Workflow:
- AI flags a threat → a human team member confirms it → a predefined playbook executes (e.g., password reset, revoke sessions, notify affected users).
Proactively Reduce Alert Noise:
- Schedule time monthly to review and tune detection thresholds.
- Whitelist known safe activities, such as automated marketing campaigns or scheduled IT tasks, to prevent unnecessary interruptions.
Maintain The Human Touch:
- When AI causes a false positive—like delaying a legitimate order—ensure your customer messaging is empathetic and clear.
- This preserves trust and demonstrates that a real person is ultimately in charge.
This collaborative approach ensures that you benefit from AI’s scalability without sacrificing the judgment and customer relationship management that only your people can provide.
With this human-AI partnership defined, it’s also crucial to understand the legal and compliance framework that governs your actions during a security incident.
Breach & Compliance Basics for Singapore SMEs
As you invest in AI security, you must stay within Singapore’s compliance and ethical framework. Below are crucial rules and guardrails to follow.
PDPA and Breach Notification
Singapore’s Personal Data Protection Act (PDPA) mandates that organisations protect personal data with “reasonable security” and notify PDPC and affected individuals within three calendar days if a notifiable breach occurs.
A breach is notifiable when it is likely to cause significant harm or affects at least 500 individuals. This short timeline makes fast AI threat detection and a prepared incident response plan critical.
Practices like encryption and least-privilege access are fundamental to meeting this “reasonable security” standard.
(Source: PDP Commission Singapore)
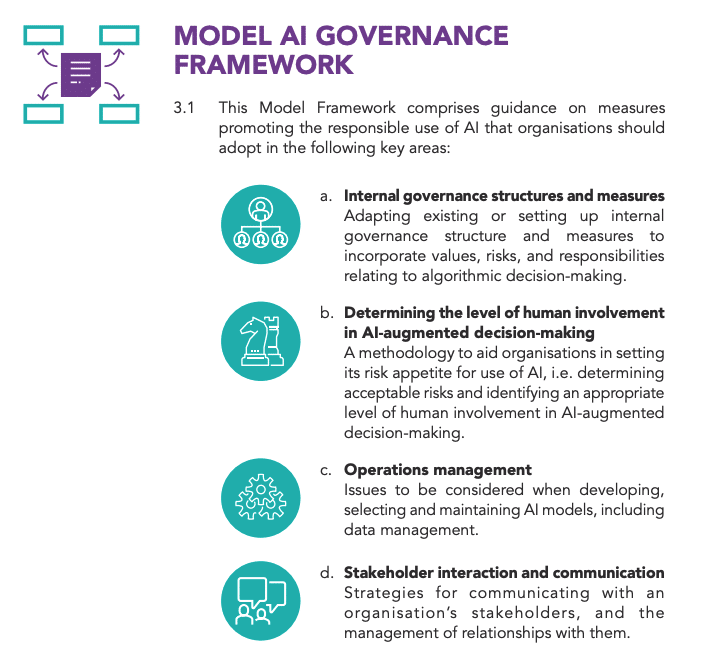
AI Governance and Explainability
Singapore’s Model AI Governance Framework promotes responsible AI use. When an AI security tool automatically blocks a transaction or flags an account, you should be able to explain that decision or have a clear process for human review.
Document how your AI systems handle data, how they are audited, and what safeguards are in place. If your team uses external AI tools, establish a policy to prevent sensitive data from being leaked into these systems.
Sectoral Cyber Rules
Your industry may impose specific rules beyond the PDPA. Fintechs, for example, must follow MAS’s Technology Risk Management guidelines.
In the event of a breach, regulators will examine whether your cybersecurity defences and overall governance were adequately implemented.
It is vital to choose AI security tools that comply with your industry’s standards and to maintain detailed logs and audit trails as evidence of your diligence.
Vendor and Data Risk
When using cloud-based or third-party AI services, your responsibility remains. Ensure your contracts explicitly cover vendor cooperation during security investigations, data residency requirements, and liability allocations.
Never assume the vendor assumes all risk; if your customer data is leaked from their platform, your SME will be held accountable for the lapse.
Understanding these rules ensures your AI adoption is not only effective but also legally sound. With these guardrails in mind, you can now build a practical and compliant rollout plan.
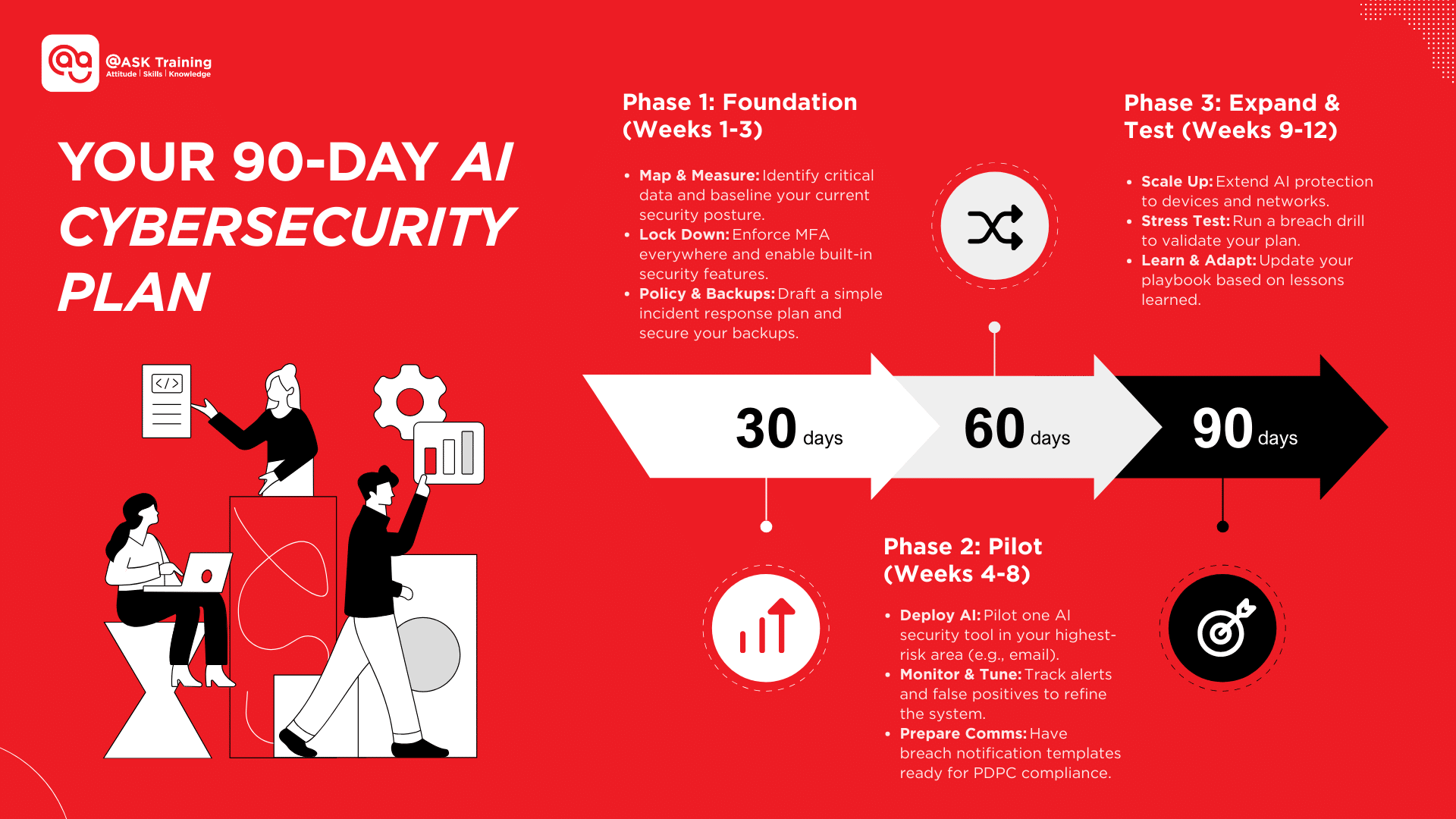
A 90-Day Playbook for Singapore SMEs
This practical, phased plan will guide you in implementing AI-powered security, building a strong defensive foundation within a single quarter.
Phase 1 (Weeks 1–3): Foundations and Risk Mapping
- Start by identifying your most critical data and systems.
- Create a short cybersecurity policy that defines roles, access rules, incident workflows, and AI usage.
- Baseline your phishing click rate with a test and measure your current detection and containment times.
- Turn on MFA everywhere, enable all built-in email and device protection features in your existing software, and ensure backups are working and isolated from production systems.
Phase 2 (Weeks 4–8): Pilot AI Controls
- Select the highest-risk area in your business, such as email or login systems, and deploy one AI-enhanced solution.
- Monitor its alerts, false positives, and response times.
- Prepare breach communication templates and escalation rules to ensure you can notify PDPC within required timelines if necessary.
- Keep humans in the loop for confirmation and review.
Phase 3 (Weeks 9–12): Expand and Test
- Extend AI-based protection to endpoints and networks.
- Consider managed detection and response (MDR) services with AI-enabled monitoring for continuous coverage.
- Run a simulated incident or tabletop exercise to validate your processes.
- Review results and update your playbook based on lessons learned.
After 90 days, you should have solid protection, better awareness, and a structure you can continuously improve.
Download this checklist to keep track of your progress!
To secure ongoing investment, the next step is demonstrating the tangible value these measures deliver.
Provide ROI with Simple Metrics
To validate your cybersecurity investment and secure an ongoing budget, focus on these key business-focused metrics.
Detection & Response Metrics
- Track reduction in phishing click rates and an increase in employee reporting after enabling AI filtering.
- Measure time-to-detect and time-to-contain incidents before versus after implementing automation.
Prevention & Financial Metrics
- Monitor the percentage of risky logins successfully challenged by MFA.
- Calculate the value of fraudulent orders blocked versus those later approved after review.
- Quantify reduced downtime and decrease scam-related support tickets.
Continuous Improvement
- Review these metrics monthly to demonstrate clear business value.
- Use the data to justify expanding successful AI security tools to other areas.
Showing how one AI control prevented a significant financial loss makes the ROI undeniable.
While these metrics prove current value, looking ahead ensures your defences remain effective against evolving threats.
Future-Proofing For The Next 10-20 Years
The cybersecurity landscape will continue evolving rapidly. Building adaptable defences today positions your SME for long-term resilience.
AI Evolution & Human Oversight
- Expect AI-versus-AI battles where automated systems fight threats in milliseconds.
- Maintain human oversight for final approval on critical decisions like fund transfers.
- Balance automation with human judgment for customer-facing communications.
Advanced Threat Preparedness
- Prepare for sophisticated deepfakes and synthetic identities in daily operations.
- Implement multi-layer verification like callback codes for payment changes.
- Assume voice and video can be faked—build verification into all sensitive processes.
Continuous Security Updates
- Schedule regular reviews of encryption standards during technology refreshes.
- Document security changes in plain English that all staff can understand.
- Treat security as an ongoing process, not a one-time project.
Building these practices today creates a foundation that adapts to tomorrow’s threats. This forward-looking approach ensures your SME remains protected as technology continues to advance.
Wrapping Up
For Singapore SMEs, embracing AI in cybersecurity is no longer a strategic advantage—it is an operational necessity.
This playbook outlines a clear path: leverage AI security tools for their unparalleled speed in threat detection and containment, while empowering your people to make informed judgments and maintain customer trust.
The time for planning is over; the time for action is now. Begin your journey this month by activating one key control, rehearsing your incident response plan, and committing to regular metric reviews.
These deliberate steps build a powerful, human-AI partnership that will safeguard your business, your customers, and your future!
Ready to Build Your Team’s Cybersecurity Expertise?
Explore @ASK Training’s industry-relevant IT and cybersecurity courses to empower your people with the skills to implement your defence strategy effectively:
Individual Upskilling
Explore our industry-relevant cybersecurity bundle courses, including:
Corporate Training Solutions
Looking to train multiple team members? Our customised corporate programmes deliver tailored cybersecurity training that addresses your specific business needs and threat landscape.
Get in touch with us and build your human firewall today!
Related Courses
- IT Courses
- Cybersecurity Essentials(offered as a 3-day Modular Course for those seeking focused training)
- Cybersecurity and Ethical Hacking
◆◆◆