As a small business owner, you wear many hats. You’re the CEO, the head of sales, and sometimes even the customer service team.
The last thing you have time for is worrying about hackers. You might think, “Why would anyone target my small operation?” This is the most dangerous myth in small business cybersecurity today.
The truth is that cybercriminals aren’t just aiming for the big corporations. In fact, 43% of all cyberattacks target small and medium-sized businesses/enterprises (SMBs/SMEs).
This is a global issue that hits close to home: The Cyber Security Agency of Singapore (CSA) reports that almost 40% of cyberattacks in Singapore target SMEs, highlighting them as a significant focus of cyber threats locally.
Why is this happening? Because SMEs often have valuable data but can lack the dedicated IT security of a large enterprise.
Compounding this vulnerability, the QBE Singapore SME Survey 2024 found that less than half (47%) of SMEs are fully aware of cyber risks, with top concerns including malware, data breaches, and phishing.
This guide will cut through the noise. We’ll explain why cyberattack prevention is critical for your survival, outline the real threats, and give you actionable steps to protect your livelihood.
Think of this as your first step toward building a robust defence for your business data protection. Let’s dive in!
Why Cybersecurity Matters for Your Small Business
Let’s be clear: cybersecurity isn’t a luxury reserved for the Fortune 500 companies; it’s a fundamental part of running a modern business.
A successful attack can lead to devastating downtime, loss of revenue, significant legal penalties, and a severe erosion of trust with your customers.
Ignoring network security for a small business is like leaving your storefront unlocked overnight; sooner or later, someone will take advantage. The stakes are simply too high to ignore.
Next, we’ll tackle some of the most common misconceptions that leave smaller companies vulnerable.
Common Misconceptions About Small Business Cyber Risk
Many business owners operate under false assumptions that create open doors for attackers. Let’s debunk a few:
“We’re too small to be a target.”
Cybercriminals use automated tools to indiscriminately scan for vulnerabilities. Your size doesn’t make you invisible; it can make you look like an easier, low-risk target.
“Cybersecurity is too expensive.”
While enterprise-level solutions can be costly, the fundamental practices of good cyber hygiene are affordable and often free. The cost of a breach is always far higher than the cost of prevention.
“We outsource our IT, so we’re safe.”
While a great IT provider is essential, security is a shared responsibility among all parties. You must ensure your vendor follows best practices, as 71.4% of breaches involve suppliers or third parties.
Dispelling these myths is the first step toward building a more secure organisation.
Now that we’ve cleared the air, let’s look at the specific threats you need to watch for.
The Most Common Cyber Attacks on Small Businesses
Understanding the enemy is half the battle. Cybercriminals use predictable methods because they work. Here are the top threats to your business, according to the Small Business Cybersecurity Statistics 2025:
1. Phishing (17%)
Deceptive emails or messages that trick employees into revealing passwords or transferring money.
2. Malware (18%)
Malicious software (viruses, spyware) that infects systems through malicious links or downloads, often stealing data or taking control of devices.
3. Data Breaches (16%)
Unauthorised access to sensitive data like customer records or financial information often occurs due to weak security or human error.
4. Ransomware (10%)
A type of malware that encrypts your files and demands a ransom for their return, paralysing your operations.
5. Website Hacking (15%)
Attackers compromise your site to deface it, steal data, or distribute malware, damaging your reputation and customer trust.
6. DDoS Attacks (12%)
Overwhelming your website with fake traffic to crash it, causing downtime and lost revenue.
These attacks are not sophisticated fantasies; they are the daily tools of cybercriminals who count on your lack of preparation.
You might notice a common thread in these attacks: they often rely on human action to succeed.
The Critical Role of Human Error in Cyber Incidents
Did you know that 74% of data breaches involve the human element?
From using weak passwords to clicking on malicious links or ignoring software updates, well-meaning employees can accidentally create a security gap.
In fact, one report found that 89% of businesses see human error as their biggest cyber risk.
This isn’t about blaming your team; it’s about empowering them. The goal is to build a culture where security is everyone’s responsibility, turning your employees from a potential vulnerability into your first line of defence.
This reliance on human error is a key reason why cybercriminals find small businesses so appealing.
Why Cybercriminals Target Small Businesses
So, why do cybercriminals target small business ventures?
It boils down to a simple calculation of risk versus reward. Attackers perceive SMEs as having weaker defences and smaller security budgets, making them easier to breach.
There’s also a lower risk of exposure for the attacker compared to targeting a high-profile corporation with a dedicated security team.
Understanding their motives is important, but let’s talk about what really matters: the impact on your business.
The Financial and Reputational Cost of a Cyberattack
The numbers speak for themselves. The median ransom demand for SMEs is around SG$365,565. But the ransom is just the beginning.
When you factor in downtime, recovery efforts, and lost business, the total cost can balloon to SGD 1.35 million or more (The Straits Times, 2025).
Beyond the financial hit, the long-term reputational damage can be even more devastating. Losing the trust of your clients can lead to customer churn that takes years to recover from.
The good news is that you don’t need a million-dollar budget to fight back. Let’s explore more in the next section.
Practical Cybersecurity Measures for Your Business
Knowing the risks is one thing; taking action is another. Effective cyber-attack prevention for small businesses is built on a foundation of basic, consistent practices.
Here are actionable steps you can implement to strengthen your business data protection:
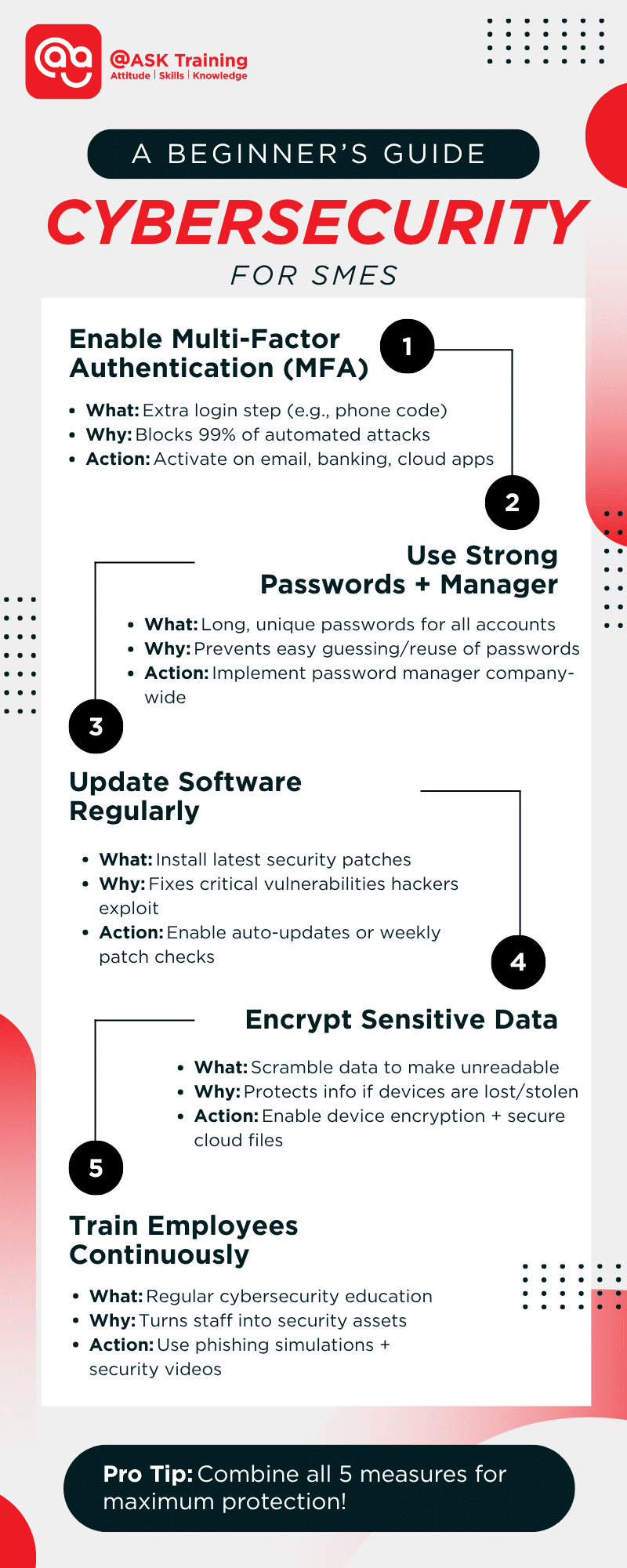
1. Enable Multi-Factor Authentication (MFA) Everywhere
- What it is: A second layer of security, like a code sent to your phone, required to log in.
- Why it matters: Blocks over 99% of automated attacks, even if a password is stolen.
- Action: Turn on MFA for email, banking, cloud storage, and any critical business software.
2. Enforce a Strong Password Policy
- What it is: Using long, complex, and unique passwords for every account.
- Why it matters: Prevents hackers from easily guessing or reusing compromised passwords.
- Action: Use a reputable password manager to generate and store strong passwords for your team.
3. Commit to Regular Software Updates
- What it is: Installing the latest patches for operating systems, apps, and plugins.
- Why it matters: Updates often fix critical security holes that hackers exploit.
- Action: Enable automatic updates wherever possible, or schedule a weekly “patch check.”
4. Encrypt Sensitive Data
- What it is: Scrambling data so it’s unreadable without a special key.
- Why it matters: Protects information if a device is lost or stolen.
- Action: Enable full-disk encryption on all laptops and use encryption for sensitive cloud files.
5. Provide Ongoing Employee Training
- What it is: Regular, engaging education on threats like phishing and safe online habits.
- Why it matters: Turns your team from a potential vulnerability into your first line of defence.
- Action: Use short videos and simulated phishing tests to build a security-aware culture. Consider implementing a formal cybersecurity training programme to ensure consistent knowledge across your team.
Implementing these measures dramatically reduces your risk, but it’s also crucial to have a plan for if things go wrong.
Building an Incident Response Plan
Even with the best prevention, you need a plan for the worst-case scenario. An incident response plan is your calm-in-the-chaos roadmap, ensuring you take the right actions quickly to minimise damage.
According to regulations like Singapore’s PDPA, a delay can be costly, with many breaches requiring disclosure to authorities within 72 hours.
Here is a simple, step-by-step framework to build your plan:
Step 1: Preparation – Before an Incident Happens
This is the most critical phase. Don’t wait for a breach to figure this out.
- Assemble Your Team: Designate who is in charge. This includes a lead decision-maker, IT support (internal or your managed provider), and a communications lead.
- Maintain Backups: Ensure you have recent, secure, and tested backups of all critical data. A backup you can’t restore is useless.
- Have Contact Lists Ready: Keep a list of contacts for your bank, legal counsel, cybersecurity insurance, and relevant authorities like the Cyber Security Agency of Singapore (CSA).
Step 2: Detection & Analysis – Identify the Scope
When you suspect an incident, your goal is to confirm it and understand its scale.
- Contain the Threat: Immediately isolate affected systems. This may mean disconnecting a computer from the network or taking a compromised website offline to prevent the attack from spreading.
- Assess the Damage: Determine what was accessed or stolen. Was it customer data, financial records, or intellectual property? Gather all the facts.
Step 3: Containment, Eradication & Recovery – Regain Control
Once you understand the breach, you can work to fix it.
- Eradicate the Threat: Remove the malicious software or close the vulnerability that was exploited. This might involve wiping and rebuilding infected machines.
- Recover Systems: Carefully restore operations using your clean backups. Monitor systems closely to ensure the threat is truly gone.
Step 4: Post-Incident Activity – Learn and Improve
After the immediate fire is put out, the review process begins.
- Notify Stakeholders: Communicate transparently with affected customers, partners, and employees, following legal requirements.
- Report to Authorities: If personal data was breached, report it to the relevant bodies within the mandated timeframe.
- Conduct a Review: Hold a “lessons learned” meeting. What worked well in your response? What could be improved? Use this to update and strengthen your plan for the future.
Having a plan empowers you to act decisively. For many small businesses, executing this plan effectively involves leveraging external expertise.
Leveraging Third-Party Security Support
You’re an expert in your business, not necessarily in IT security. For many small and medium-sized businesses, building a robust internal security posture is a significant challenge.
This is where leveraging third-party security support becomes a strategic advantage. Partnering with a Managed Service Provider (MSP) or a dedicated cybersecurity firm can provide you with enterprise-level expertise without the cost of a full-time, in-house team.
When considering external support, focus on these key points:
1. When to Seek Help
If you lack dedicated IT staff, feel overwhelmed by the technical aspects of network security for a small business, or simply want to ensure your foundational defences are professionally managed, it’s time to explore third-party options.
2. What to Look for in a Provider
- Proven Expertise: Look for providers with experience in your industry and verifiable credentials.
- Clear Communication: They should explain risks and solutions in plain language, not technical jargon.
- Robust Security Posture: Ask about their own security practices; your safety depends on theirs.
3. Secure the Partnership Contractually
- Ensure your service-level agreement (SLA) clearly outlines their responsibilities for monitoring, response times, and data protection.
- Verify that contracts include specific obligations for securing your data, ensuring they are a true partner in your business data protection efforts.
Engaging the right third-party support is a great step in strengthening your small business cybersecurity, allowing you to focus on growing your business with greater confidence.
Wrapping Up
The digital landscape is always changing, and so are the threats. The key takeaway is that small business cybersecurity is not a one-time project but an ongoing process of vigilance and adaptation.
By understanding the risks, implementing practical measures, and fostering a culture of security, you can significantly reduce your chances of becoming a statistic.
Your business is your passion. Protect it proactively!
Your Cyber Resilience is an Ongoing Journey
@ASK Training specialises in empowering businesses with the knowledge they need to thrive securely.
We go beyond theory to provide practical, hands-on learning in areas like cybersecurity awareness, data protection, and operational excellence.
Here are a few essential Cybersecurity courses to explore:
Our programmes can be customised to address your unique challenges. Visit our Corporate Training page or speak with our consultants to learn how we can work together to build a more secure and resilient organisation.
Related Courses
- IT Courses
- Cybersecurity Essentials(offered as a 3-day Modular Course for those seeking focused training)
- Cybersecurity and Ethical Hacking
◆◆◆
Related Articles
Article Topics
- Why Cybersecurity Matters for Your Small Business
- Common Misconceptions About Small Business Cyber Risk
- The Most Common Cyber Attacks on Small Businesses
- The Critical Role of Human Error in Cyber Incidents
- Why Cybercriminals Target Small Businesses
- The Financial and Reputational Cost of a Cyberattack
- Practical Cybersecurity Measures for Your Business
- Building an Incident Response Plan
- Leveraging Third-Party Security Support
- Wrapping Up