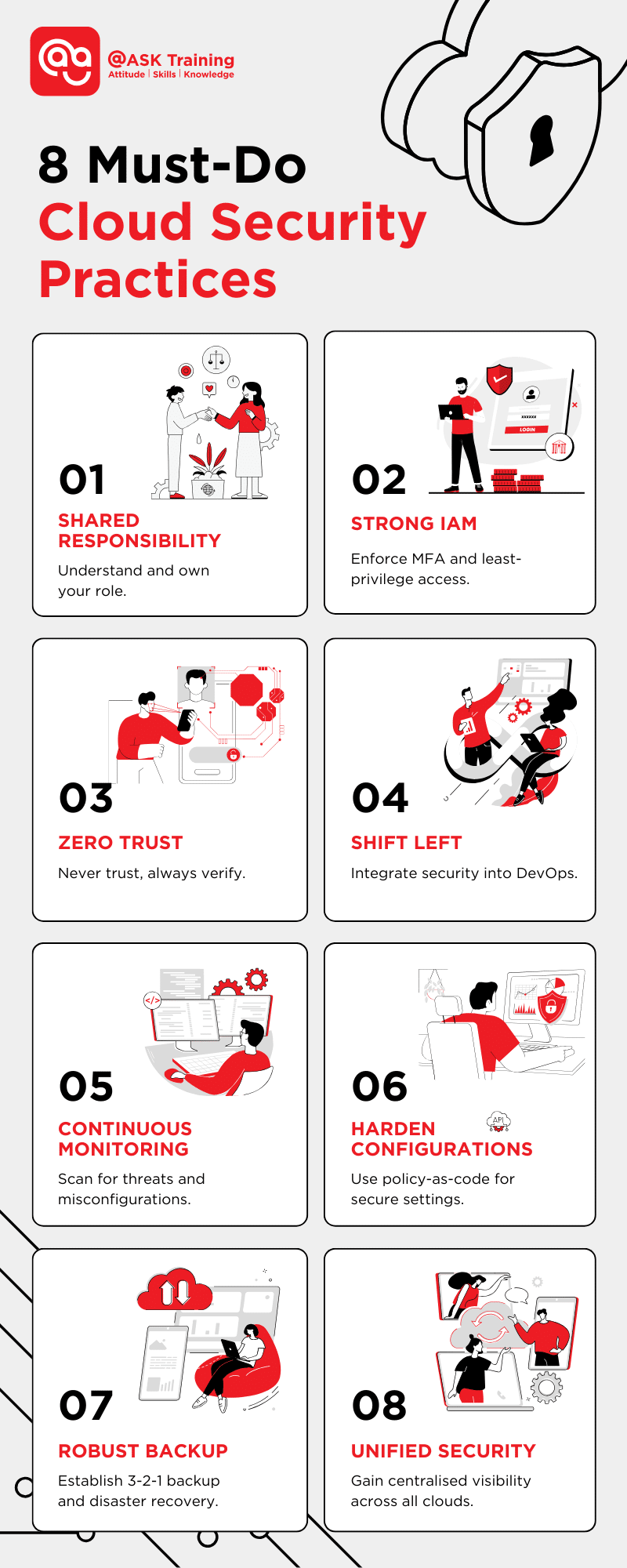
The cloud has transformed how businesses operate, offering unprecedented scalability and flexibility. However, this transformation also introduces complex security challenges.
In 2025, with the rise of multi-cloud and hybrid environments alongside a growing remote workforce, effective cloud security is more critical than ever.
This article will equip cloud and IT professionals with current, actionable cloud cybersecurity practices for protecting data, applications, and infrastructure in these complex, distributed environments.
Let’s get started!
#1 Understand and Own the Shared Responsibility Model
When we talk about cloud security, it’s really a shared responsibility. A partnership between you, the customer, and your cloud provider.
We often see security gaps emerge when teams mistakenly assume coverage without truly verifying who is responsible for what.
The division of responsibility actually varies depending on the service model you’re using:
- Infrastructure as a Service (IaaS): Here, you’re responsible for managing the operating system, your data, and access controls.
- Software as a Service (SaaS): In this model, the provider handles the underlying infrastructure, but you still maintain control over identity and the data you input.
Recommendation:
Regularly review your provider’s shared responsibility model and adjust your internal controls accordingly, especially when you’re adopting new services. It’s a crucial step to ensure there are no unnoticed gaps in your security posture.
Now that we’ve clarified the foundational shared responsibility, let’s dive into how to manage access within your cloud environment.
#2 Implement Strong Identity and Access Management (IAM)
Robust IAM is truly fundamental to securing your cloud environment. It’s about ensuring the right people have the right access, and nothing more.
Multi-Factor Authentication (MFA)
This is non-negotiable. Require MFA for all accounts – that includes users, administrators, and even third-party integrations.
Least-Privilege Access
This principle means granting users and services only the precise permissions they need to perform their specific tasks, and nothing more.
For instance, you might grant administrative privileges for a very specific one-hour maintenance window, then automatically revoke them right after to minimise exposure.
Access Review Automation
Automating your access reviews is incredibly helpful. It flags excessive, unused, or risky permissions.
Imagine identifying accounts with admin access that haven’t been used in 30 days. Automation can then remediate this by removing or downgrading those permissions.
Tools
Consider leveraging powerful tools below to manage and analyse your permissions effectively:
With strong IAM in place, the next logical step is to build a security perimeter that assumes no one is inherently trusted.
#3 Adopt a Zero Trust Cloud Security Model
Zero trust cloud security is a security framework that operates on a power principle:
“Never trust, always verify”
This means that every user, device, application, and workload must rigorously prove its identity and context before access is granted, regardless of its network location.
Micro-Segmentation
Think about applying micro-segmentation within your cloud environment.
For example, you can isolate development, testing, and production environments into entirely separate virtual networks, each with its own specific access policies and monitoring controls.
Conditional Access Policies
A practical example of this is using conditional access policies to allow sign-ins only from managed, compliant devices located within specific geographic regions.
If a device is jailbroken, outdated, or connecting through unknown IPs, access is simply denied.
Identity-Based Controls
Emphasise using identity-based controls and real-time telemetry to create dynamic, context-aware security boundaries.
This could mean requiring re-authentication if a user’s behaviour deviates from their usual patterns, such as trying to access sensitive resources they typically don’t use.
Check out our comprehensive guide on What is Zero Trust Security where we discuss the steps to building a Zero-Trust Architecture.
Moving beyond establishing a dynamic security perimeter, let’s explore how to embed security earlier in your development processes.
#4 Shift Left: Integrate Security into DevOps Pipelines
Embedding security earlier in the development lifecycle, what we call “shifting left,” is crucial for efficiency and effectiveness.
Automated Scans
The idea is to integrate automated scans directly into your CI/CD pipelines. This means scanning application code, container images, and infrastructure-as-code (IaC) before anything is even deployed.
Prevent Secret Leaks
Here’s a clear example:
Configure your pipeline to automatically fail if sensitive secrets like AWS credentials or private keys are accidentally committed to the repository, using tools like GitGuardian or truffleHog.
Early Detection
The ultimate goal is to identify and address misconfigurations, secrets, and vulnerabilities before they reach production.
This significantly reduces the cost and complexity of fixing issues later on.
Once security is built into your development processes, the next critical step is to constantly watch for threats and anomalies in your live environment.
#5 Enable Continuous Monitoring and Threat Detection
Continuous monitoring is absolutely vital for maintaining a strong cloud cybersecurity posture. You can’t protect what you can’t see.
Cloud-Native Tools
We highly recommend using cloud-native security tools such as:
These tools continuously scan for threats, misconfigurations, and anomalous behaviour across your cloud environments.
Key Monitoring Areas
What should you be looking for? Focus on suspicious IAM activity (like privilege escalations), failed or unusual login attempts, and access originating from unexpected geographic locations.
Alerting
A practical example:
Configure alerts for critical events, such as S3 buckets that suddenly become public, or for IAM roles that are modified outside approved change windows, using services like AWS CloudTrail or Azure Monitor.
Beyond just monitoring, let’s consider how to proactively strengthen the very foundation of your cloud infrastructure.
#6 Harden Secure Cloud Configurations and Secure APIs
Maintaining secure cloud configurations and ensuring robust API security are paramount for preventing breaches.
Configuration Management Tools
Utilise tools like AWS Config, Azure Policy, or GCP Config Validator to continuously scan for insecure settings.
This includes things like unencrypted EBS volumes, publicly accessible S3 buckets, or open security groups.
Policy-as-Code
Think about policy-as-code as writing your security rules directly into code (using tools like Terraform or OPA) that are then automatically enforced.
For example, you could deny the deployment of an AWS S3 bucket if encryption isn’t enabled.
API Security
When it comes to APIs, examples of securing them include:
- Implementing rate limiting (such as limiting requests to 100 per minute per IP)
- Using WAF rules to block SQL injection attempts
- Employing schema validation tools like OpenAPI to reject malformed input before it can be executed.
Even with the strongest configurations, unexpected events can occur, which brings us to the importance of robust recovery plans.
#7 Establish Robust Backup and Disaster Recovery Plans
Effective cloud data protection relies heavily on comprehensive backup and disaster recovery strategies. You need to be prepared for the worst.
3-2-1 Backup Rule
We strongly advise following the 3-2-1 backup rule:
- Keep at least three copies of your data
- Stored in two different formats (e.g., disk and cloud)
- With one copy stored offsite or in a different cloud region.
This protects you against localised failures.
Regular DR Testing
Run disaster recovery (DR) tests quarterly. This isn’t just a formality; it’s to verify that your backups are restorable, that your recovery point objectives (RPO) and recovery time objectives (RTO) are achievable, and that all dependencies (like DNS and IAM) are covered in your plan.
Secure Backup Access
It’s crucial to secure access to your backups. This means requiring MFA, restricting roles, and logging all backup-related activity to prevent insider threats or the compromise of your backups themselves.
Finally, for organisations operating across multiple cloud platforms, it’s vital to bring all these security efforts together.
#8 Unify Security Across Multi-Cloud Security Strategies & Hybrid Environments
For organisations utilising multi-cloud security strategies or hybrid environments, a unified approach to security isn’t just a nice-to-have; it’s essential.
Unified Security Platforms
We recommend using unified security platforms like:
These platforms help you gain centralised visibility, ensure consistent policy enforcement, and provide robust threat detection across all your environments.
Centralised Posture Management
As an example, you can use a Cloud-Native Application Protection Platform (CNAPP) to view your security posture across AWS, Azure, and GCP from a single dashboard.
This can quickly surface issues like open ports, misconfigured IAM roles, or unencrypted databases.
Reduced Blind Spots
Ultimately, consolidating your monitoring and controls significantly reduces blind spots, simplifies audits, and improves response times in these increasingly complex environments.
Wrapping Up
So, what have we learned about navigating the complexities of cloud security in 2025? We’ve covered eight essential practices that are truly non-negotiable for protecting your data, applications, and infrastructure.
Here’s a quick recap of the must-do cloud security practices we explored:
- Understand and Own the Shared Responsibility Model: Know who is responsible for what, avoiding critical security gaps.
- Implement Strong Identity and Access Management (IAM): Enforce MFA for all accounts and practise least-privilege access, automating reviews to prevent excessive permissions.
- Adopt a Zero Trust Security Model: Operate with a “never trust, always verify” mindset, employing micro-segmentation and conditional access.
- Shift Left: Integrate Security into DevOps Pipelines: Embed automated security scans early in the development lifecycle to catch issues before production.
- Enable Continuous Monitoring and Threat Detection: Use cloud-native tools to constantly scan for threats, misconfigurations, and anomalous behaviour across cloud environments.
- Harden Cloud Configurations and Secure APIs: Proactively enforce secure settings using policy-as-code and robust API protection measures.
- Establish Robust Backup and Disaster Recovery Plans: Implement the 3-2-1 backup rule and conduct regular DR tests, securing backup access.
- Unify Security Across Multi-Cloud and Hybrid Environments: Gain centralised visibility and consistent policy enforcement using unified security platforms.
In essence, what ties all these practices together is the understanding that effective cloud security is continuous, automated, and identity-driven—it’s not a one-time setup.
By embracing these strategies, your organisation can significantly enhance its cloud compliance and confidently protect its valuable assets in the evolving digital landscape.
Ready to Upskill Your Cloud Security?
In today’s rapidly evolving digital landscape, cloud security expertise is no longer optional; it’s a career-defining necessity.
@ASK Training is here to empower professionals like you with industry-aligned IT courses that transform theoretical knowledge into real-world defensive skills.
Explore our Cloud, Automation and Emerging Tech courses, including:
Enrol with us today and take the next step in your cloud security journey!
Related Courses
◆◆◆
Related Articles
Article Topics
- #1 Understand and Own the Shared Responsibility Model
- #2 Implement Strong Identity and Access Management (IAM)
- #3 Adopt a Zero Trust Cloud Security Model
- #4 Shift Left: Integrate Security into DevOps Pipelines
- #5 Enable Continuous Monitoring and Threat Detection
- #6 Harden Secure Cloud Configurations and Secure APIs
- #7 Establish Robust Backup and Disaster Recovery Plans
- #8 Unify Security Across Multi-Cloud and Hybrid Environments
- Wrapping Up