Cyber threats are evolving at a pace that is becoming increasingly complex to detect. This is where cybersecurity becomes a priority. Protecting an organisation’s critical assets and actively preventing any unauthorised access requires addressing these threats head-on.
Understanding the principles of access control can strengthen your organisation’s security posture and mitigate potential risks. This article will explore the fundamentals of access control, its key components, types, and best practices.
If you’re a cybersecurity student, a mid-career professional, an IT manager, or a business executive, this guide will provide you with the foundational knowledge and practical insights needed to implement and manage access control strategies effectively.
Let’s start with the basics.
What is Access Control?
Access control is a security measure that limits who can view, use, or modify restricted in an IT network or system. It’s like a gatekeeper, ensuring only users that are given authority or access can enter. This applies to both in physical and digital environments.
For example, a physical access control system might use key cards to restrict entry to a building. In contrast, digital access control systems might use passwords to protect access to a computer network.
By using access control, organisations can protect their sensitive information and systems from unauthorised physical and digital access.
Now that we’re clear on what is access control, the next section will explore what are the key components of access control.
Key Components of Access Control
To effectively implement access control, several key components must work together seamlessly. These components include:
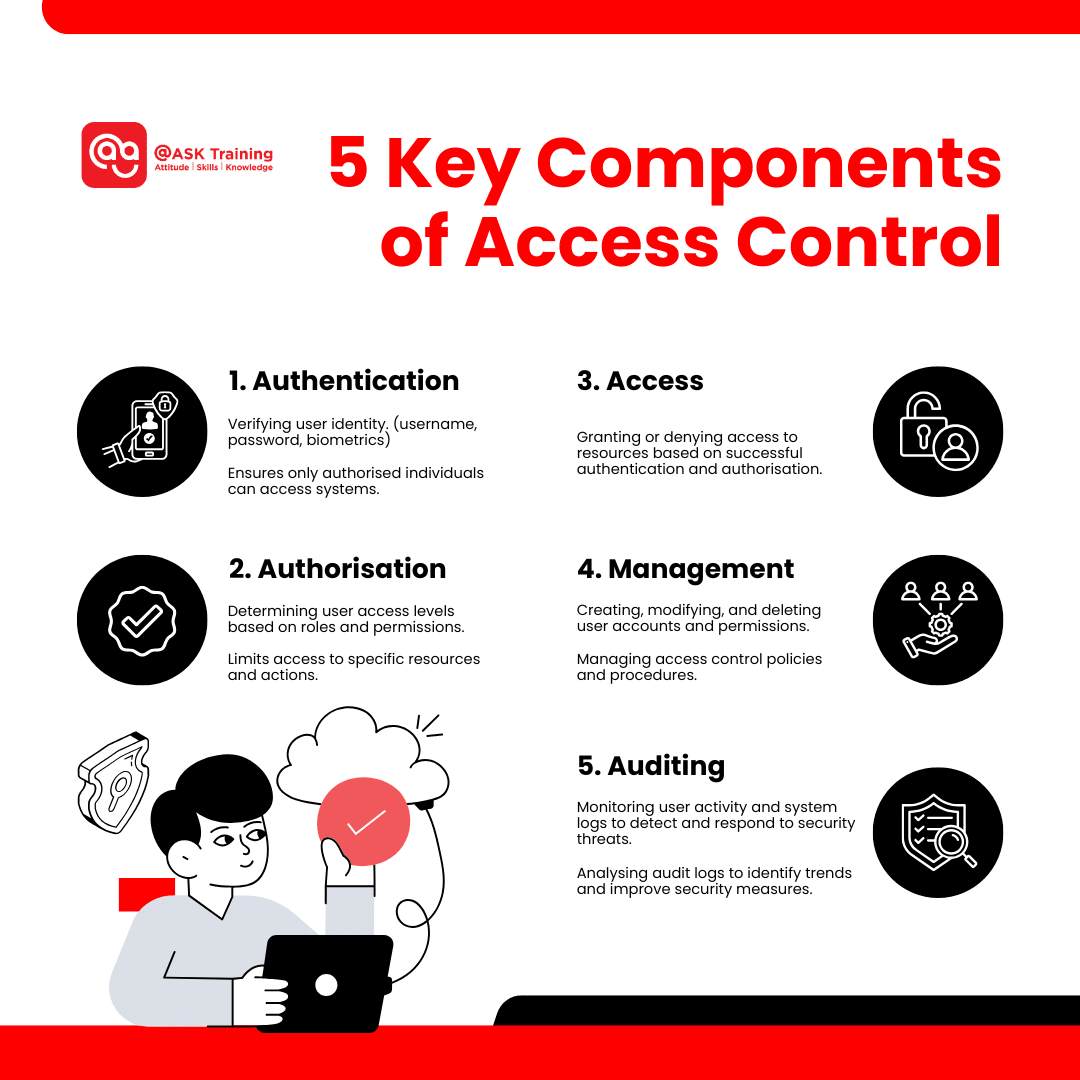
Authentication
Authentication is the process of confirming a user’s identity by verifying credentials such as usernames, passwords, or biometric information. For example, a user must provide a username and password to access a computer system.
Authorisation
Once a user’s identity is verified, authorisation determines their level of access to specific resources based on their role. This is based on predefined rules and policies. For instance, a system administrator might have full access to all system resources, while a regular user can only access certain files and applications.
Access
This is the actual granting or denying of access to a resource based on the user’s authentication and authorisation. If a user is successfully authenticated and authorised, they will be granted access to the requested resource. Otherwise, access will be denied.
Management
This includes managing user accounts, permissions, and access control policies. This involves creating new accounts, modifying existing ones, assigning permissions, and updating policies as necessary.
Auditing
The auditing process involves monitoring and logging user activities to detect and prevent any unauthorised access. By reviewing audit logs regularly, security teams can identify suspicious activities and take appropriate action.
By understanding these key components, you can help organisations implement effective access control strategies to protect their valuable assets.
Why is Access Control Important
Access control is a cornerstone of cybersecurity, safeguarding sensitive information and systems from unauthorised access. Let’s explore further why access control is essential for several reasons:
Protecting Sensitive Data and Resources
By limiting access to authorised individuals, organisations can safeguard sensitive data and resources from unauthorised access, theft, and misuse. This helps to protect intellectual property, financial information, and other valuable assets.
Supporting Regulatory Compliance
Many industries have stringent data privacy and security regulations, such as:
- PDPA (Personal Data Protection Act): Singapore’s data protection law that regulates the collection, use, and disclosure of personal data.
- MAS (Monetary Authority of Singapore): Regulates financial institutions and requires them to implement strong security measures, including access control.
- Cybersecurity Authority of Singapore (CSA): Provides cybersecurity guidelines and standards, including access control requirements.
- PCI DSS (Payment Card Industry Data Security Standard): For organisations that process credit card payments.
- HIPAA (Health Insurance Portability and Accountability Act): For healthcare organisations that handle protected health information (PHI).
- SOC 2 (Service Organisation Controls 2): For service organisations that store customer data in the cloud.
- ISO 27001: A global standard for information security management systems.
Implementation of robust access control measures are core requirements for organisations can comply to these regulations and standards.
Reducing Security Risks and Data Breaches
By minimising the number of individuals who have access to sensitive information and systems, organisations can reduce the risk of human error, insider threats, and external attacks.
This can help prevent data breaches, which can have significant financial and reputational consequences.
Now that we understand the importance of access control, let’s delve deeper into the different types of access control that organisations can implement.
Types of Access Control
There are several types of access control, each with its own advantages and disadvantages. Here are some of the most common types:
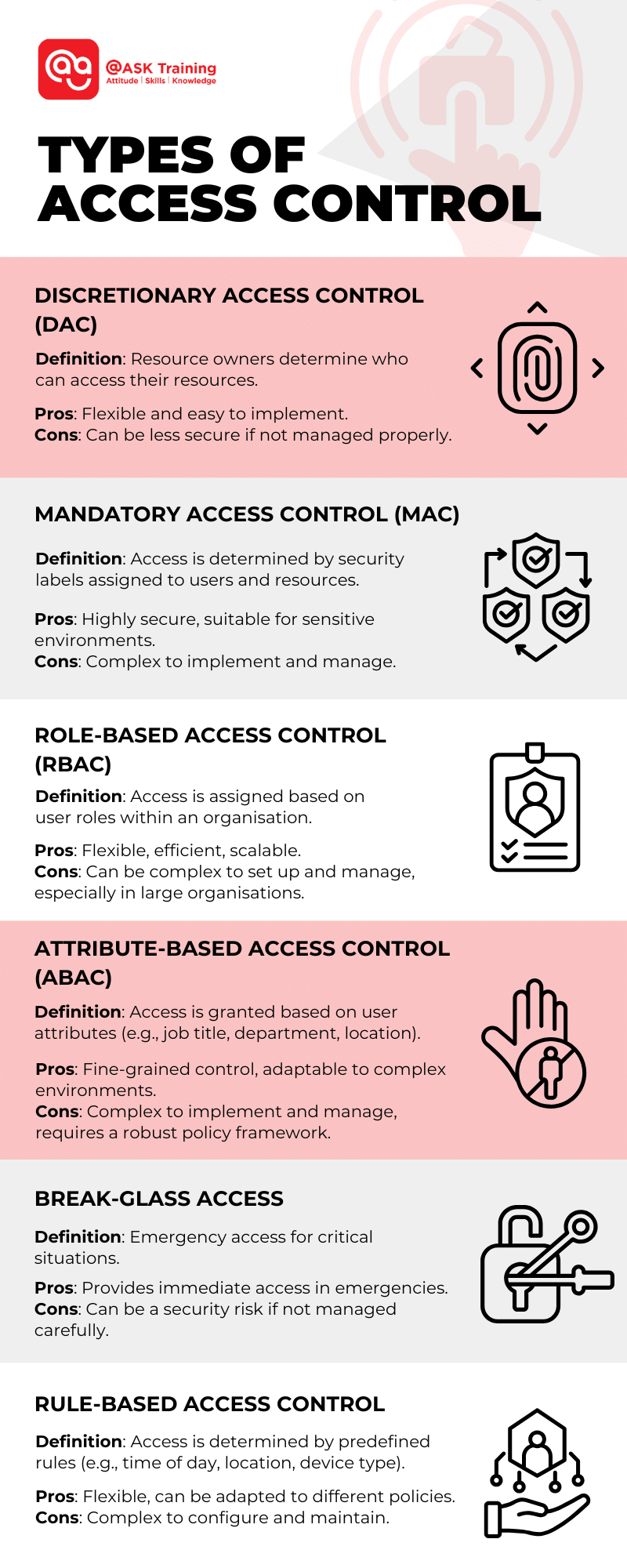
Discretionary Access Control (DAC)
In DAC, the owner of a resource determines who has access to it. This is a flexible approach, but it can also lead to security vulnerabilities if not managed properly.
For example, a user might accidentally grant too much access to another user, or a malicious user might exploit vulnerabilities in the system.
- Pros: Flexible and easy to implement.
- Cons: Can be less secure if not managed properly.
Mandatory Access Control (MAC)
MAC is a more restrictive approach where access is determined by security labels assigned to users and resources. This can be helpful in highly secure environments, such as government agencies or military organisations. However, it can also be complex to implement and manage.
- Pros: Highly secure and can be used in sensitive environments.
- Cons: Complex to implement and manage.
Role-Based Access Control (RBAC)
RBAC is a popular approach that assigns permissions based on a user’s role within an organisation. For example, a system administrator might have full access to all system resources, while a regular user might only be able to access certain files and applications.
RBAC is a flexible and efficient way to manage access control, as it allows organisations to easily assign permissions to users based on their job roles.
- Pros: Flexible and efficient, can be easily scaled to accommodate organisational changes.
- Cons: Can be complex to set up and manage, especially in large organisations.
Attribute-Based Access Control (ABAC)
ABAC is a more advanced approach that grants access based on user attributes, such as their job title, department, or location. This can be helpful for organisations with complex security requirements, as it allows for fine-grained control over access.
For example, a policy might be created to allow only employees in the finance department to access sensitive financial data.
- Pros: Fine-grained control over access, can be adapted to complex security requirements.
- Cons: Can be complex to implement and manage, and requires a robust policy framework.
Break-Glass Access
This type of access is used in emergency situations, such as a major system outage or a security breach. It allows authorised personnel to bypass regular access controls to gain immediate access to critical systems or data.
While useful in emergencies, it’s important to implement strict controls to prevent unauthorised access.
For example, a system administrator might need to access a critical system during off-hours to resolve an urgent issue. In such a case, they could use break-glass access to bypass regular authentication and authorisation controls.
- Pros: Provides emergency access to critical systems and data.
- Cons: This can be a security risk if not managed carefully.
Rule-Based Access Control
This type of access control uses predefined rules to determine who can access what resources. These rules can be based on factors such as time of day, user location, or device type.
For example, a rule might allow employees to access certain systems only during business hours and from company-issued devices.
- Pros: Flexible and can be adapted to different security policies.
- Cons: Can be complex to configure and maintain.
By understanding these different types of access control, you can choose the best approach for your organisation’s specific needs.
Now that we’ve explored the different types of access control, let’s discuss some practical tips for implementing effective access control strategies.
Implementing Access Control
To effectively implement access control, organisations can leverage various tools and strategies:
Methods
VPNs (Virtual Private Networks)
VPNs create secure, encrypted connections between devices and networks, protecting sensitive data transmitted over public networks. This ensures that only authorised users can access company resources, even when working remotely.
Password Management Tools
These tools help users create, store, and manage strong, unique passwords for different accounts. By using strong, complex passwords, organisations can reduce the risk of unauthorised access.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a code generated by a mobile app. This makes it much harder for attackers to compromise accounts, even if they have stolen a password.
Identity and Access Management (IAM) Solutions
IAM solutions provide centralised management of user identities and access permissions, simplifying the process of granting and revoking access. This helps to ensure that only authorised users have access to the resources they need.
Steps for Effective Implementation
Step 1: Identify Critical Assets
Determine which assets are most valuable and require the highest level of protection. This helps to focus security efforts on the most important assets.
Step 2: Conduct a Risk Assessment
Evaluate potential threats and vulnerabilities to identify areas where access control is most needed. This helps to prioritise security measures and allocate resources effectively.
Step 3: Define Access Policies
Develop clear and concise access control policies that outline who can access what resources and under what conditions. These policies should be regularly reviewed and updated to reflect changes in the organisation’s needs.
Step 4: Implement Authentication and Authorisation Mechanisms
Choose appropriate authentication methods (e.g., passwords, biometrics) and authorisation mechanisms (e.g., role-based access control) to enforce access policies. This ensures that only authorised users can access the resources they need.
Step 5: Monitor and Audit
Continuously monitor user activity and system logs to detect and respond to security incidents. By monitoring user behaviour and system activity, organisations can identify and address potential threats early on.
Step 6: Regularly Review and Update Access Controls
As business needs and security threats evolve, it’s important to review and update access control policies and procedures. This helps to ensure that access controls remain effective and up-to-date.
Importance of Zero-Trust Architecture:
In today’s complex and dynamic digital landscape, a zero-trust architecture is becoming increasingly important.
This approach assumes that no internal user or device is inherently trustworthy, and it requires continuous verification and authorisation before granting access to resources. By adopting a zero-trust approach, organisations can significantly enhance their security posture and reduce the risk of breaches.
If you’d like to learn more on how you can build a zero-trust architecture for your organisation, check out our previous post on What is Zero Trust Security?
By following these best practices and leveraging the latest technologies, organisations can implement robust access control measures to protect their sensitive information and systems.
Now that we’ve explored the fundamentals of access control, let’s look at some real-world examples to illustrate its application.
Real-World Examples of Access Control
Access control is all around us, both in the physical and digital realms. Here are some common examples:
Physical Access Control
Physical access control systems are designed to restrict entry to specific areas or buildings. Here are a few examples:
Public Housing Access Cards

Housing Access Cards Example
(Source: Gateway Lock and Key)
How it Works: Public housing access cards use RFID technology to verify resident identities. When a resident swipes their card at a designated reader, the system checks their access privileges and grants or denies entry.
Benefits:
- Enhanced security: Restricts access to authorised residents only.
- Convenience: Eliminates the need for physical keys.
- Efficiency: Streamlines the entry process.
Example: Housing Development Board (HDB) Singapore implements robust access control systems in public housing estates to ensure the safety and security of residents.
EZ-Link Card Readers

(Source: Land Transport Guru)
These devices are used to control access to MRT stations and buses, allowing only those with valid tickets to board.
How it Works: EZ-Link card readers use contactless technology to verify the validity of EZ-Link cards. When a passenger taps their card on the reader, the system deducts the fare and grants access to the bus or MRT train.
Benefits:
- Efficient boarding: Streamlines the boarding process, reducing waiting times.
- Contactless payment: Reduces the risk of transmission of germs.
- Cashless transactions: Promotes a cashless society.
Office Building Access Control

Example of Access Control for Office Buildings
(Source: Gunnebo)
How it Works: Office buildings often use a combination of access control technologies, such as key cards, biometric scanners, and mobile access apps. These systems restrict entry to authorised personnel, ensuring the security of sensitive information and assets.
Benefits:
- Enhanced security: Prevents unauthorised access to the building and restricted areas.
- Improved visitor management: Streamlines the visitor registration and sign-in process.
- Remote access control: Enables remote management of access permissions.
Security Industry Association (SIA) provides insights into the latest access control technologies and best practices for office buildings, helping organisations protect their assets and employees.
Logical Access Control
Logical access control is crucial for protecting sensitive information and ensuring that only authorised users can access specific digital resources. Here are a few examples:
SingPass
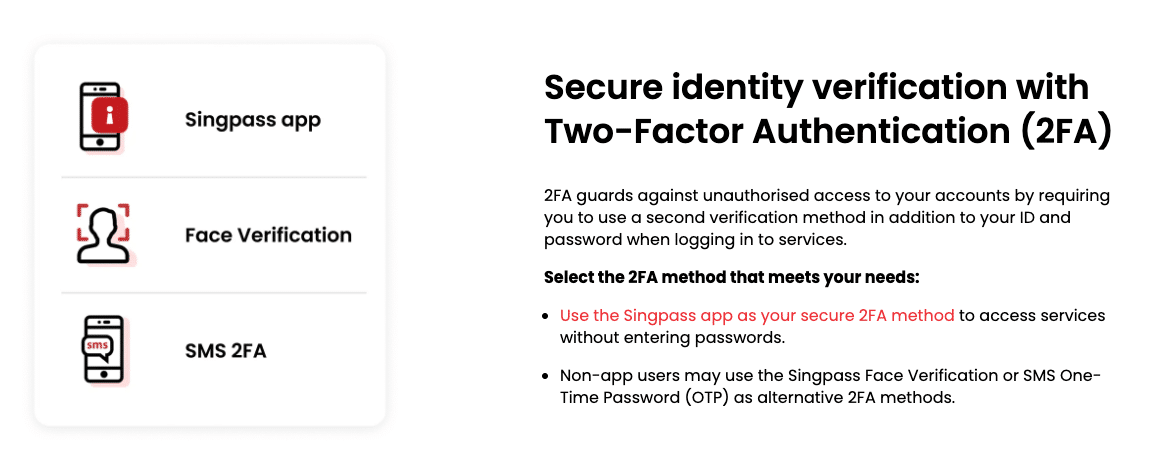
SingPass’s Two-Factor Authentication
(Source: SingPass)
How it Works: SingPass is Singapore’s national digital identity system that requires users to authenticate themselves through strong passwords and two-factor authentication (2FA) to access government services.
Benefits: This system enhances security by reducing the risk of unauthorised access and protecting sensitive personal information.
NETS and PayNow

(Source: NETS)
How it Works: NETS and PayNow are electronic payment systems that use strong authentication protocols and encryption to secure financial transactions. Users are required to authenticate themselves using various methods, such as passwords, SMS OTPs, or biometrics.
Benefits: These systems protect sensitive financial information and ensure the security of online transactions.
Corporate Network Access
How it Works: Many companies in Singapore use firewalls, intrusion detection systems (IDS), and other security measures to protect their corporate networks from unauthorised access. These systems monitor network traffic, identify potential threats, and block malicious activity.
Benefits: These measures help to protect sensitive corporate data and prevent unauthorised access to company resources.
Example: Cyber Security Agency of Singapore (CSA) provides guidelines and best practices for organisations to enhance their network security, including the use of firewalls and IDS.
Additionally, organisations can implement Information Security Management Systems (ISMS) to further strengthen their security posture.
These examples demonstrate how access control is used to safeguard physical and digital resources, ensuring that only authorised individuals can gain access.
Challenges in Access Control
While access control is essential for security, organisations face several challenges in implementing and managing it effectively:
Managing Distributed IT Environments
As more and more organisations move their operations to the cloud and adopt a microservices architecture, they face the challenge of managing and securing a growing number of digital identities.
For example, according to Cloud Security Alliance, organisations may struggle to implement consistent access control policies and monitor privileged access effectively, increasing the risk of unauthorised access and data breaches.
User Fatigue from Passwords
The increasing number of online accounts we have today leads to a problem known as “user or password fatigue.”
A research article in the Journal of Cybersecurity highlights the issue of user fatigue from passwords in today’s digital world, where users are required to manage numerous accounts with complex passwords.
This can lead to several negative consequences:
- Weak Passwords: When users have to remember a large number of passwords, they might resort to creating weak or easily guessed passwords to simplify the process. This makes them more vulnerable to hacking attempts.
- Password Reuse: Users might reuse the same password across different accounts for convenience. However, if one account gets compromised, attackers can gain access to other accounts protected by the same password.
- Password Sharing: Frustrated by remembering numerous passwords, users may resort to sharing their credentials with colleagues or writing them down in insecure locations, further increasing security risks.
Integration with Cloud Services
As organisations increasingly adopt cloud-based services, integrating access control with these services can become complex. This is particularly challenging due to the diverse range of identity providers and security protocols used by different cloud service providers.
Here are some specific challenges:
- Connecting Different Systems: It can be difficult to connect your organisation’s internal systems with the cloud service to ensure smooth access for employees.
- Data Privacy and Security: Different cloud services have different rules about how your data is protected. Ensuring that your data is safe and compliant with regulations can be complex.
- Keeping Up with Changes: Cloud services are always changing and updating. Keeping track of these changes and making sure your access controls are always up-to-date can be a challenge.
Ensuring User Experience
While strong security is essential, it’s important to avoid making the user experience too difficult or frustrating. Overly complex access controls can lead to:
- User Frustration: Complicated login processes and frequent password resets can annoy users and lead to decreased productivity.
- Workarounds: Frustrated users may resort to less secure methods, such as sharing passwords or writing them down, to bypass complex security measures.
- Security Risks: Workarounds can introduce security vulnerabilities, making it easier for attackers to exploit weaknesses in the system.
By carefully addressing these challenges, organisations can implement robust access control measures that protect their sensitive information and systems.
To achieve this, let’s explore the best practices for effective access control in the next section.
Best Practices for Access Control
To address these challenges and ensure effective access control, organisations should follow these best practices:
Enforce the Principle of Least Privilege (PoLP)
Grant users only the minimum level of access necessary to perform their job functions. This reduces the risk of unauthorised access and data breaches. For example, a regular employee might only need access to specific files and applications, while a system administrator would have broader access.
Use Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide two or more forms of identification, such as a password and a code generated by a mobile app. This makes it much harder for attackers to compromise accounts, even if they have stolen a password.
Conduct Regular Security Audits
Regularly assess your organisation’s security posture to identify and address vulnerabilities. This includes reviewing access control policies, user permissions, and system logs.
Implement Strong Password Policies
Enforce strong password policies that require users to create complex passwords, such as a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, passwords should not be recycled and should also be changed regularly.
Employee Awareness Training
Train users on security best practices, such as avoiding phishing attacks, recognising social engineering tactics, and reporting suspicious activity.
Incident Response Plan
Have a plan in place to respond to security incidents, such as data breaches or unauthorised access. This plan should outline steps to contain the incident, investigate the cause, and restore normal operations.
Leverage Identity and Access Management (IAM) Solutions
IAM solutions can help streamline access control processes, automate tasks, and improve security. For example, IAM solutions can automate user provisioning, de-provisioning, and password resets, reducing the burden on IT teams.
Consider Zero-Trust Architecture
A zero-trust architecture assumes that no user or device is inherently trustworthy. By implementing a zero-trust approach, organisations can significantly enhance their security posture.
Wrapping Up
By following these best practices, organisations can establish robust access control measures that protect their sensitive information and systems while minimising user inconvenience.
In conclusion, access control plays a vital role in safeguarding sensitive information and resources in any organisation. Key points to remember include:
- Definition: Access control is a security mechanism that regulates access to physical and digital resources.
- Components: Authentication and authorisation are the two main components of access control.
- Types: Access control can be physical (e.g., key cards, biometrics) or logical (e.g., passwords, firewalls).
- Best Practices: Implementing strong password policies, using multi-factor authentication, conducting regular security audits, and leveraging IAM solutions are essential for effective access control.
By following these best practices and staying informed about emerging threats, organisations can significantly enhance their security posture and protect their valuable assets.
To delve deeper and stay ahead of evolving cyber threats, consider exploring additional resources such as:
- National Institute of Standards and Technology (NIST): NIST provides comprehensive guidelines and standards on cybersecurity, including access control.
- Open Web Application Security Project (OWASP): OWASP offers valuable insights into web application security, including access control best practices.
- Cybersecurity & Infrastructure Security Agency (CISA): CISA provides guidance and resources on cybersecurity, including access control.
Remember, a strong security posture is a continuous effort. By prioritising access control and staying informed, you can help your organisation stay protected in today’s digital world.
Ready To Strengthen Your Organisation’s Security Posture?
@ASK Training offers comprehensive Cybersecurity courses suitable for beginners and advanced learners. Our Cybersecurity courses are designed to help you gain the knowledge and skills you need to protect yourself and your organisation’s valuable assets.
Get in touch and enrol with us today!
Related Courses
◆◆◆
