In today’s interconnected world, technology has become an integral part of our lives. We rely on computers and networks for everything from work and education to entertainment and social interactions. However, with this increased reliance comes a heightened risk of cyberattacks.
In this article, we will explore cybersecurity fundamentals for beginners, discuss common cyber threats, and provide practical tips to help you protect yourself and your data in the digital age.
The Growing Threat Landscape in Singapore
The cybersecurity landscape in Singapore is characterised by the rising frequency and severity of cyberattacks.
According to Singapore’s Cyber Security Agency (CSA)’s Cybersecurity Health Report 2023, over 80% of organisations in Singapore encountered a cybersecurity incident within a year, with many experiencing multiple incidents. Common threats include ransomware and social engineering scams.
The financial impact of these attacks is substantial, with the average cost of a cybersecurity breach in Singapore reaching approximately SGD 1.7 million (USD 1.3 million) per breach.
This makes Singapore one of the regions with the highest costs associated with cyberattacks in Asia-Pacific. With the alarming spread of cyber threats, penetration testing has become an essential component of a robust cybersecurity strategy.
This article will provide a comprehensive overview of penetration testing, explaining what it is, how it is conducted, and why it is essential for safeguarding your systems.
What is Penetration Testing
Penetration testing is a simulated cyberattack conducted on a computer system to identify and exploit vulnerabilities. It involves ethical hackers using the same tools and techniques as malicious actors to uncover weaknesses in a system’s security defences.
Think of pen testing as a controlled attack on your systems. Ethical hackers, also known as penetration testers (pentesters), simulate real-world cyberattacks to uncover weaknesses in your defences.
It’s like a security fire drill but for your organisation’s digital infrastructure! The goal? To identify and exploit these vulnerabilities before malicious actors can, allowing you to patch those holes and strengthen your overall security posture.
Types of Penetration Testing
Not all pen tests are created equal. Different types cater to specific needs. Here’s a quick rundown:
| Type | Description | Example |
|---|---|---|
| Internal Pen Test | Simulates attacks from within the organisation’s network | A pentester gains unauthorised access from a compromised workstation |
| External Pen Test | Mimics attacks from external sources like the internet | A pentester exploits vulnerabilities in a public-facing web application |
| Blind Pen Test | Provides minimal information to the pentester | A pentester is given only the organisation’s public IP and domain name |
| Double-Blind Pen Test | Keeps both parties unaware of each other | A third party coordinates the test, providing minimal information to both the pentester and the organisation |
| Social Engineering | Targets human vulnerabilities | A pentester tricks employees into revealing information or clicking malicious links |
| IoT Pen Test | Assesses the security of IoT devices | A pentester compromises smart home devices to gain network access |
| Network Pen Test | Evaluates network infrastructure security | A pentester exploits vulnerabilities in network routers or firewalls |
| Web Application Pen Test | Assesses web application security | A pentester injects malicious code into a web application to steal data or gain access |
| Physical Pen Test | Examines physical security of facilities and infrastructure | A pentester bypasses physical security measures to gain unauthorised access to premises |
By simulating various attack scenarios, penetration testing can help organisations improve their breach detection systems and incident response plans.
With a solid understanding of the various types of penetration testing, we can now examine the detailed process that pentesters follow to assess your organisation’s security posture.
The Penetration Testing Process
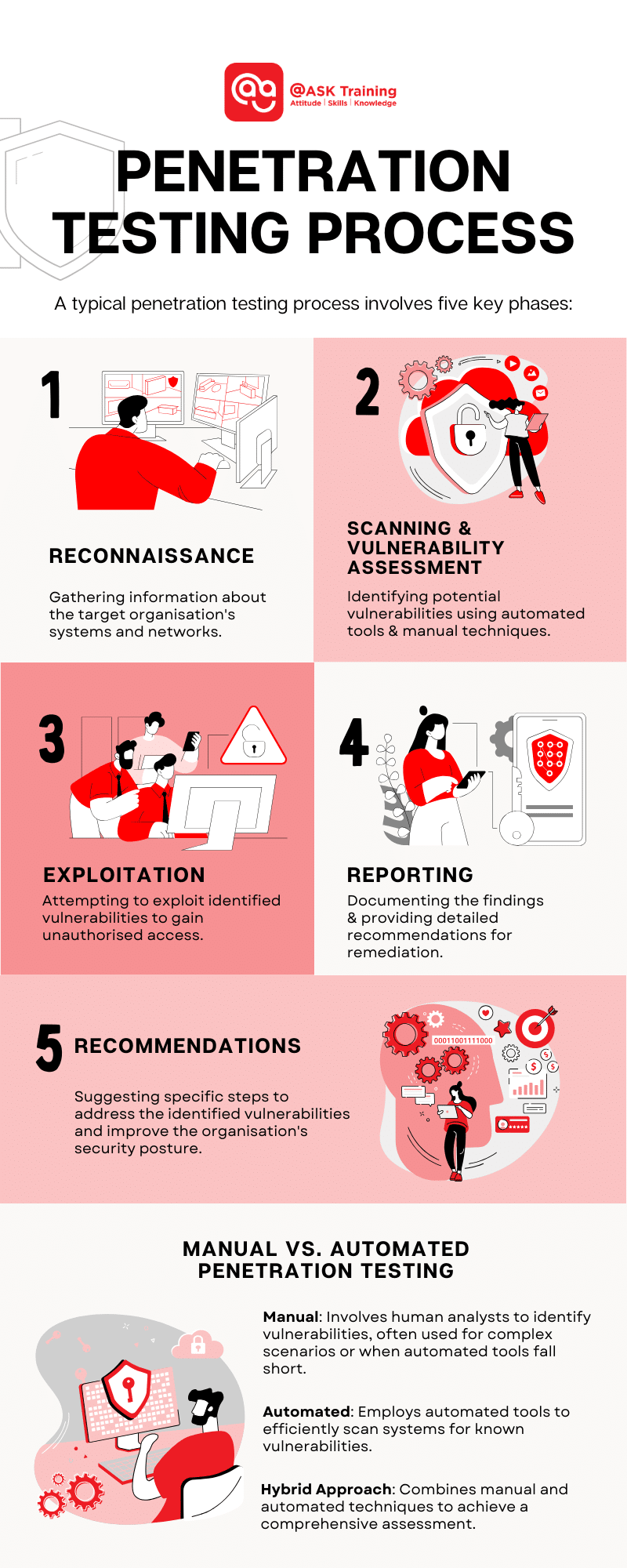
A typical penetration testing process involves five key phases:
1. Reconnaissance
- Gathering Intel: Pentesters meticulously gather information about your organisation’s systems, networks, and public-facing assets.
- Footprinting: This involves techniques like domain name system (DNS) lookups, WHOIS searches, and social media analysis to identify potential entry points.
- Example: A pentester might use tools like Nmap or Shodan to scan your network for open ports and services.
2. Scanning and Vulnerability Assessment
- Automated Tools: Pentesters employ automated tools to scan your systems for known vulnerabilities, including vulnerability scanning and security analysis.
- Manual Verification: Human expertise is crucial to identify less obvious vulnerabilities and assess the potential impact of discovered issues.
- Example: A pentester might use tools like Nessus or Metasploit to identify vulnerabilities in your web applications, network devices, or operating systems.
3. Exploitation
- Testing the Waters: Pentesters attempt to exploit identified vulnerabilities to assess their impact and gain unauthorised access.
- Ethical Hacking: This phase simulates real-world attacks, helping organisations understand the potential consequences of vulnerabilities.
- Example: A pentester might exploit a SQL injection vulnerability in your web application to steal sensitive data or gain unauthorised access to your database.
4. Reporting
- Detailed Findings: Pentesters document their findings in a comprehensive report, outlining the vulnerabilities discovered, their severity, and potential impact.
- Recommendations: The report provides actionable recommendations to address the identified vulnerabilities and improve your security posture.
- Example: A report might include details about discovered vulnerabilities, such as cross-site scripting (XSS) or remote code execution (RCE), along with specific steps to remediate them.
5. Recommendations
- Tailored Solutions: Pentesters offer tailored recommendations based on their findings, helping organisations prioritise remediation efforts.
- Continuous Improvements: The recommendations aim to enhance your organisation’s overall security posture and reduce the risk of future breaches.
- Example: A pentester might recommend patching vulnerable software, implementing stronger access controls, or conducting regular security awareness training for employees.
Manual vs. Automated Penetration Testing
While automated tools can efficiently scan for vulnerabilities, manual testing provides a more in-depth and nuanced assessment. A combination of both approaches is often recommended to achieve the best results.
While both manual and automated penetration testing play crucial roles in assessing security posture, they have distinct advantages and disadvantages:
Automated Tools
Efficiently scan for known vulnerabilities and provide a baseline assessment.
Pros:
- Flexibility: Human analysts can adapt to changing circumstances and identify non-standard vulnerabilities.
- Creativity: Pentesters can think outside the box and devise innovative attack techniques.
- In-Depth Analysis: Manual testing allows a deeper understanding of system behaviour and potential attack vectors.
Cons:
- Time-Consuming: Manual testing can be time-consuming, especially for large-scale assessments.
- Human Error: Human error can lead to missed vulnerabilities or inaccurate evaluations.
- Cost: Manual testing can be more expensive due to the labour involved.
Manual Testing
Can identify more subtle vulnerabilities and assess the potential impact of discovered issues.
Pros:
- Efficiency: Automated tools can quickly scan systems for known vulnerabilities.
- Consistency: Automated tests can be repeated consistently to identify new vulnerabilities.
- Cost-Effective: Automated tools can reduce the cost of penetration testing.
Cons:
- Limited Scope: Automated tools may not identify complex or novel vulnerabilities.
- False Positives: Automated tools can sometimes generate false positives, requiring manual verification.
- Dependency on Tool Capabilities: The effectiveness of automated testing relies on the capabilities of the tools used.
Hybrid Approach
Combining automated and manual testing can provide a more comprehensive and effective assessment.
This approach leverages the strengths of both methods to provide a comprehensive assessment of an organisation’s security posture.
By understanding the penetration testing process and the interplay between manual and automated techniques, organisations can make informed decisions about their cybersecurity strategy and proactively protect their valuable assets.
Why is Penetration Testing Important?
Penetration testing offers a multitude of benefits for organisations of all sizes. Here’s why:
Identifying and Mitigating Security Vulnerabilities
- Unmasking Hidden Weaknesses: Beyond the obvious, while automated tools can identify common vulnerabilities, manual penetration testing can uncover hidden weaknesses that might otherwise go unnoticed.
- Human Intuition: Pentesters apply their expertise and experience to simulate real-world attacks, often finding vulnerabilities that automated tools might miss.
- Proactive Defence: By Identifying vulnerabilities before they can be exploited, penetration testing enables organisations to take proactive steps to protect their sensitive data and systems.
- Preventing Breaches: Addressing vulnerabilities can significantly reduce the risk of data breaches, which can have devastating consequences for businesses.
Meeting Regulatory Compliance and Industry Standards
- Regulatory Adherence: Penetration testing is often required to comply with industry regulations and standards, such as the Singapore Personal Data Protection Act (PDPA).
- Demonstrating Due Diligence: Penetration testing can help organisations demonstrate that they have taken reasonable steps to protect their data and systems.
- Avoiding Fines and Penalties: Non-compliance with industry regulations can lead to significant fines and penalties. Penetration testing can help organisations avoid these risks.
- Building Trust: By demonstrating that you have implemented appropriate security measures, penetration testing can help build trust with customers, partners, and stakeholders.
By investing in regular penetration testing, organisations can significantly reduce their risk of data breaches, protect their reputation, and ensure compliance with industry regulations.
With a clear understanding of the benefits of penetration testing, let’s explore how it can be used alongside other security measures to protect your organisation.
Penetration Testing and Other Security Measures
To achieve comprehensive security, penetration testing should be used in conjunction with other security measures. One such essential tool is a Web Application Firewall (WAF).
How Penetration Testing and WAFs Work Together
- Complementary Roles: WAFs act as a first line of cyber defence, blocking common web application attacks in real-time. Penetration testing, on the other hand, provides a more in-depth assessment of your security posture.
- Identifying Vulnerabilities: Penetration testing can uncover vulnerabilities that WAFs might miss, such as complex attacks or custom-crafted exploits.
- Testing WAF Effectiveness: Pentesters can evaluate the effectiveness of your WAF by attempting to bypass its protections.
- Leveraging WAF Data: For many times of pen testing (except blind and double-blind tests), pentesters can use WAF logs to identify potential vulnerabilities and tailor their attacks accordingly.
A Stronger Defence Together
By combining penetration testing with WAFs, organisations can create a more robust and effective defence against cyber threats. WAFs can help prevent common attacks, while penetration testing can identify advanced threats and ensure that your WAF is configured correctly.
Now that we’ve discussed the importance of combining penetration testing with other security measures, let’s explore some real-world examples of how organisations are using penetration testing to protect their assets.
Real-World Applications of Penetration Testing in Singapore
Penetration testing has become an indispensable tool for organisations across various sectors in Singapore. Here are some real-world examples of how different industries utilise and apply penetration testing to enhance their cybersecurity:
Financial Services
Purpose: Protect sensitive financial data and comply with regulatory requirements.
Application:
- Safeguarding Customer Data: Banks and financial institutions use penetration testing to protect sensitive customer data, such as account numbers, credit card information, and transaction history.
- Compliance: Regular assessments ensure adherence to stringent regulations like the Monetary Authority of Singapore (MAS) requirements, demonstrating a commitment to data protection.
- Simulated Attacks: By mimicking the tactics of cybercriminals, banks and financial institutions can evaluate the effectiveness of their security measures against real-world threats.
E-Commerce and Retail
Purpose: Safeguard customer information and payment systems.
Application:
- Protecting Customer Information: Online retailers rely on penetration testing to safeguard customer data, including personal information, payment details, and purchase history.
- Preventing Fraud: Regular assessments help identify vulnerabilities that could be exploited by cybercriminals to steal customer data and commit fraud.
- Web Application Testing: E-commerce platforms in Singapore strengthen their security posture and protect against online threats, such as SQL injection attacks and cross-site scripting (XSS) vulnerabilities.
Healthcare
Purpose: Protect patient data and comply with health regulations.
Application:
- Safeguarding Patient Data: Penetration testing is crucial for healthcare organisations to protect sensitive patient data, including medical records, insurance information, and personal identifiers.
- Internal Penetration Testing: Healthcare organisations assess their internal networks to prevent unauthorised access to sensitive patient information.
- Compliance: Adhering to regulations like the Personal Data Protection Act (PDPA) is essential for healthcare providers. Penetration testing helps demonstrate compliance and reduces the risk of fines and penalties.
Telecommunications
Purpose: Secure network infrastructure against unauthorised access.
Application:
- Network Penetration Testing: Telecom companies conduct thorough assessments of their network security configurations and security protocols to identify vulnerabilities that could be exploited by attackers.
- Incident Response Preparation: By understanding potential entry points, telecom providers can better prepare for incidents and enhance their overall security strategies.
Government Agencies
Purpose: Protect sensitive government data and maintain public trust.
Application:
- Comprehensive Security Assessments: Government entities conduct penetration tests to evaluate the security of public-facing applications and internal systems, ensuring they are resilient against cyber threats.
- Protecting Sensitive Data: Government agencies use penetration testing to safeguard sensitive government information, such as national security secrets and citizen data.
- The Singapore Cyber Security Agency (CSA): Implemented a framework for cybersecurity service providers, including penetration testing companies. This framework ensures that service providers meet the necessary standards and qualifications to deliver effective penetration testing services to government agencies.
Education
Purpose: Safeguard student information and research data.
Application:
- Vulnerability Scanning and Testing: Educational institutions perform penetration tests to identify weaknesses in their IT infrastructure, protecting sensitive data from breaches.
- Awareness Programmes: Many universities also implement cybersecurity awareness programmes alongside technical assessments to educate staff and students about potential threats.
By identifying vulnerabilities and strengthening defences, penetration testing is a critical component of a robust cybersecurity strategy for organisations across various sectors in Singapore.
Wrapping Up: Is Your Organisation Safe from Cyber Threats?
Cyber threats are becoming increasingly sophisticated. Organisations in Singapore cannot afford to neglect their cybersecurity any longer. Penetration testing offers a powerful tool for identifying vulnerabilities, strengthening defences, and protecting sensitive data.
We’ve explored the importance of penetration testing in today’s cybersecurity landscape and here are the key takeaways:
- Penetration testing is a crucial tool for identifying and mitigating security vulnerabilities.
- Different types of penetration testing cater to specific needs, such as internal, external, blind, double-blind, social engineering, IoT, network, web application, and physical.
- The penetration testing process involves reconnaissance, scanning and vulnerability assessment, exploitation, reporting, and recommendations.
- A combination of manual and automated testing is often recommended for optimal results.
- Penetration testing helps organisations meet regulatory compliance requirements and improve their overall security posture.
- It’s essential to use penetration testing in conjunction with other security measures, such as WAFs, for a comprehensive defence.
Empower Your Team!
To ensure your organisation is well-equipped to address the ever-evolving cybersecurity landscape, consider investing in cybersecurity training for your employees.
@ASK Training offers comprehensive Cybersecurity courses designed to equip individuals with the knowledge and skills needed to protect your organisation from threats.
Our Cybersecurity courses are also eligible for SkillsFuture and PSEA funding. Courses include:
Get in touch with us and enrol today! Take the first step towards a more secure future!
Related Courses
◆◆◆
